| Navigation | |
Assessing the Security of Navigation System A case study using enhanced Loran
One detection method is to examine PPM pulses. Since the TOA of PPM pulses are not known a priori, the effect of the overlay cannot be predicted. Given tonal spoofing, the spoofer effects depend on the data symbol on carried by the PPM pulse. Hence, the spoofer cannot control the outcome. Using 9th pulse modulation as an example, spoofing a 300 m error will result in certain symbols being shifted by one while others will be unchanged as seen in Figure 3.
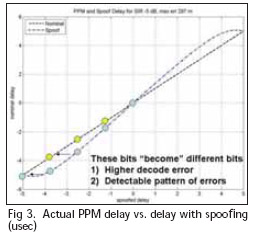
The spoofing is detectable since the symbol errors are systematic and occurs at a high rate. The discrepancy can be checked by the receiver by comparing its actual error rate to expected error rate. With cross checking of modulated pulses, the maximum range error that can be induced is about 250 m or less.
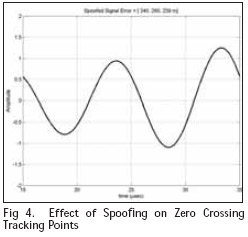
Spoofing also leave other traces on the signal that can be checked. One detection method is to examine multiple tracking point. A short monopole is narrowband and hence difficult to “instantaneously” turn on and off. As a result, spoofing will likely affect multiple Loran cycles. Even if the relative phase between a likely spoof signal and the Loran signal is maintained, the Loran signal envelope changes resulting in a different spoofed “error” at each tracking point. The deviation can be derived by both analysis and simulation. Figure 4 shows an example from simulation. In the figure, spoofing a 239 m error on the 30 microsec (sixth zero crossing) tracking point results in a 280 m error at the 25 microsec (5th zero crossing) and a 340 m error at the 20 microsec point.
Another means of spoof detection is the use of magnetic (H) field antennas. These antennas allow for the determination of received signal direction [15]. A single, on-air spoofing antenna can only generate signals from one direction. Hence a receiver designed to use an H field antenna will be able to distinguish the spoofer from the true system which would have signals coming from multiple directions. Furthermore, the receiver can check the consistency of the incoming signal directions with its calculated location.
Direct Injection Attacks
Resistance to on-air attacks is only one form of robustness. Direct injection attacks such as when the receiver is connected to a spoofing simulator also can pose a navigation security issue. Such an attack likely involves a complicit user with an incentive to deceive the navigation system. Examples include avoiding restricted zones or road toll charges. Such attacks circumvent the physical difficulties mentioned in the previous section. Other security features are necessary to mitigate such attacks. Two useful techniques for Loran to counter these attacks are: 1) authentication and 2) location dependent or hidden markers.
In the context of navigation, ideal authentication verifies the signal source and that the signal has not been maliciously delayed. The former may be provided by schemes based on data or source authentication techniques. Authenticated time dependent data reduces vulnerability to attacks where the signal is captured, stored and rebroadcasted. A symmetric key based data authentication protocol, Time Efficient Stream Losstolerant Authentication (TESLA), has been suggested for use in navigation [16] [17]. TESLA has been test implemented on Loran [9]. Another category of data authentication techniques that can be used is cryptographic signatures. Cryptographic signatures use a public-private key pair. They require distribution of a public key that is confirmed to be from the true system and a mechanism for revoking and redistributing public keys should a private key be compromised. While these systems require more processing (orders of magnitude) and longer keys than symmetric key systems, the gap can be narrowed with newer techniques such as those based on elliptic curves [18]. Both methods may be modified for eLoran and other low bandwidth navigation systems with some performance loss [19] [20].
Even with data authentication, the signal can still be delayed and quickly rebroadcast. Location dependent information and other hidden markers may be used to compliment data authentication and reduce the threat. For Loran, cross rate interference (CRI) provides one means. CRI cause different data bit errors depending on location. Receipt of the full message allows the Reed Solomon error correction to identify these interfered or “hidden” bits. Data authentication and time dependent data are needed so that a spoofer cannot generate a valid message a priori and the user can cross check the “freshness” of the message. The result is that a spoofer cannot generate the full sequence of data until after it receives the full message delaying its ability to rebroadcast. The delay from needing the full message and the time dependent information makes it difficult to trick users with reasonable knowledge of time. The weakness of CRI is that it has slow spatial decorrelation. The attacker can be several kilometers away and still experience the same CRI effects. It may be possible to augment the Loran broadcast specifically to improve the performance of the concept.
Conclusions
The article examines navigation security by using eLoran as a case study. It discusses the possible attacks that could affect the signal and user. It determines the vulnerability level and looks at available mitigations. I
n analyzing on-air attacks, the article quantifies the amount of power needed to jam or spoof Loran signals and determines the feasibility of an attacker to achieve these levels. While the required power is orders of magnitude larger than that need to jam GNSS, it is still not very large.
The difficulty in attacking Loran lies in generating the required radiated power from a short antenna. The analysis shows that generating a few milliwatts of output at low frequency on a small antenna requires significant input voltage. Hence, on-air jamming and spoofing is tremendously challenging and requires significant infrastructure to achieve. While certain forms of spoofing are easier, they still represent a significant challenge to an attacker. Even if the equipment issues can be overcome, spoofing effectiveness is limited in terms of the error inducible and detectability.
For direct injection attacks, the article examines potential defenses that are or could be incorporated into the system. It discusses techniques to aid the authentication of the Loran signal and its use with location based makers. These represent the major defense against direct injection attacks.
Disclaimer
The views expressed herein are those of the authors and are not to be construed as official or reflecting the views of the U.S. Coast Guard, Federal Aviation Administration, Department of Transportation or Department of Homeland Security or any other person or organization.
Acknowledgments
The authors gratefully acknowledge the support of the Federal Aviation Administration and Mitchell Narins under Cooperative Agreement 2000- G-028. They are grateful for the support their support of Loran and the activities of the LORIPP. The authors would also like to acknowledge Tim Hardy and John Pinks at Nautel.
Bibliography
“Vulnerability Assessment of the Transportation Infrastructure Relying on the Global Positioning System,” John A. Volpe National Transportation System Center, August 20, 2001.
Press Office, U.S. Department of Homeland Security, “Statement from DHS Press Secretary Laura Keehner on the Adoption of National Backup System to GPS,” February 7, 2008
General Lighthouse Authorities of the United Kingdom and Ireland, Research and Radionavigation, “The Case for eLoran,” Version 1.0, May 2006
Scott, L., “Anti-Spoofing & Authenticated Signal Architectures for Civil Navigation Systems”, Proceedings of the Institute of Navigation GPS Conference, Portland OR, Sept 2003
Kuhn, Mark us G., “An Asymmetric Security Mechanism for Navigation Signals”, 6th Information Hiding Workshop, 23-25 May 2004, Toronto, Canada, Proceedings, LNCS 3200, pp.239–252, Springer-Verlag.
Bowditch, Nathaniel, “Chapter 12: Loran”, The American Practical Navigator, Paradise Cay Publications, 2004
Forssell, Borje, “The Dangers of GPS/ GNSS”, Coordinates, February 2009
Humphrey, T. E., Ledvina, B. M., Psiaki, M. L., O’Hanlon, B. W., and Kintner, Jr., P. M., “Assessing the Spoofing Threat: Development of a Portable GPS Civilian Spoofer,” Proceedings of the Institute of Navigation GNSS Conference, Savannah, GA, Sept 2008
Qiu, Di, Lo, Sherman, Peterson, Benjamin, and Enge, Per, “Geoencryption Using Loran,” Proceedings of the Institute of Navigation National Technical Meeting, San Diego, CA, January 2007
International Radio Consultative Committee, “Ground-Wave Propagation Curves for Frequencies Between 10 kHz and 30 MHz”, CCIR Recommendation 368-7, Geneva last updated 1992.
Lo, Sherman and Enge, Per, “Analysis of the Enhanced LORAN Data Channel”, Proceedings of the 2nd International Symposium on Integration of LORAN-C/ Eurofix and EGNOS/Galileo, Bonn, Germany, February 2001, pp. 159-168
Hardy, T., “The Next Generation LF Transmitter Technology for (e)LORAN,” Proceedings of the Royal Institute of Navigation NAV08/International Loran Association 37th Annual Meeting, London, UK, October 2008
Stutzman, Warren L., Thiele, Gary A., Antenna Theory and Design, Second Edition, John Wiley & Sons, Inc, New York, 1998
Jordan, Ed ward C., Electronmagnetic waves and radiating systems, Second Edition, Prentice-Hall, Englewood Cliffs, NJ, 1968
Johannesse n, Erik, “Loran’s Role in Future PAT,” Proceedings of the 35th Annual Convention and Technical Symposium, Groton, CT, October 2006 (Presentation only)
Wullems, C ., Pozzobon, O., Kubik, K., “Signal Authentication and Integrity Schemes for Next Generation Global Navigation Satellite Systems,” Proceedings of the European Navigation Conference GNSS, Munich, July 2005
Perrig, A. Canetti, R., Tygar, J.D., and Song, D., “The TESLA Broadcast Authentication Protocol,” CryptoBytes, 5:2, Summer/Fall 2002, pp. 2-13
National Security Agency (NSA), The Case for Elliptic Curve Cryptography, 2009, http://www.nsa.gov/business/ programs/elliptic_curve.shtml
Becker, Georg, et. al., “Efficient authentication mechanisms: A Radio-navigation case study,” Proceedings of the Institute of Navigation GNSS Conference, Savannah, GA, September 2009
Lo, Sherman and Enge, Per, “Authenticating Aviation Augmentation System Broadcasts”, Proceedings of the Institute of Navigation/Institute of Electrical and Electronics Engineers Position Location and Navigation Symposium 2010, Indian Wells, CA May 2010
 |
|
|||||
 |
|
|||||
 |
|
My Coordinates |
EDITORIAL |
|
News |
INDUSTRY | GPS | GALILEO UPDATE | LBS | GIS | REMOTE SENSING |
|
Mark your calendar |
SEPTEMBER 2010 TO NOVEMBER 2011 |
Pages: 1 2











 (No Ratings Yet)
(No Ratings Yet)






Leave your response!