| Navigation | |
Assessing the Security of Navigation System A case study using enhanced Loran
This article assesses the security of eLoran and discusses how its features can be utilized to provide defenses against likely attacks |
|
Global Navigation Satellite Systems (GNSS) have become increasingly interwoven into the fabric of our infrastructure and economic system. However, as the services provided by GNSS become more important for safety of life and economically critical infrastructure, subversive elements will be increasingly tempted deny or spoof its signals. Given that GNSS has well-acknowledged vulnerabilities, it is becoming recognized that mitigations and back-ups are necessary [1]. Indeed, we are hopefully moving to a robust, comprehensive approach to position, navigation and timing (PNT) architecture. An element that should be central to the consideration is security. This article uses Loran as a case study for a systematic examination of navigation security. The study of interest as Loran is oft considered as a good complement to GNSS for improving overall PNT security and availability.
Loran, in particular the next generation Enhanced Loran (eLoran), has many properties that make it a good complement to GNSS. It has similar outputs and performance as GNSS. As it is an area navigation (RNAV) system, it can be used to drive the same interfaces as GNSS. eLoran is being developed to provide performance levels that can support non precision approach (NPA), harbor entrance approach (HEA), and stratum 1 frequency and precise timing. At the same time, it is an independent system and has failure modes that differ from GNSS. The attractiveness of Loran as part of a full PNT architecture has been recognized by entities such as the US Department of Homeland Security (DHS) and the General Lighthouse Authority (GLA) of England, Ireland, and Scotland [2][3]. While having a back up implies security through redundancy, the eLoran system can provide even more security to PNT. Its characteristics make many of the attacks significantly more difficult than in GNSS. Its higher power makes it more robust to on-air attacks. The system can carry signal authentication messages to dissuade other attacks. Its dissimilar characteristics makes attacking Loran technically different from attacking GNSS. eLoran, in this context, is extremely attractive as a part of a comprehensive PNT architecture. This article assesses the security of eLoran and discusses how its features can be utilized to provide defenses against likely attacks.
Navigation Security
Navigation security is increasingly important for two reasons. The first is the increased adoption and integration of navigation technologies. Navigation security is needed to ensure that the PNT outputs we count on are indeed reliable. The second is the global increase of information technology threats. Secure navigation can serve as a building block for protection of information and assets. These two distinct points can be encapsulated as “security for navigation” and “security from navigation”, respectively.
This article focuses primarily on the “security for navigation” as it is a prerequisite for “security from navigation.” To understand navigation security, it is important to understand the threats and attacks that may be inflicted upon it.
This section discusses attacks and Loran characteristics that may be useful for security. It categorizes the various possible attacks and introduces common defenses. It describes specific Loran features and how they apply to security against attacks. More background on navigation security measures and Loran are available in literature [4][5][6].
Attack Models & Common Defenses
Attack models are useful for the assessment of system robustness and are a standard tool used by the security community. In assessing the security of a radio-navigation system, we divide the attacks into two major categories – on-air and off air attacks. On-air attacks are ones where the adversary attempts to compete with or overwhelm the broadcast signal. Off air or direct injection attacks are ones where the adversary directly inputs into the receiver.
On-air attacks can come in several forms. One common category of GNSS attack is jamming. Jamming is the broadcast of RF power that interferes with a receiver’s ability to track the genuine signals resulting in denial of service (DoS). Many incidences of GNSS jamming have been reported. The other major category of on-air attack is broadcast spoofing where a competing signal is transmitted so that the user receiver generates an incorrect position. This threat is real and there have been anecdotal accounts of GNSS spoofing as well as spoofer demonstrations [7][8]. Different spoofing techniques exist. The transmission of simulated signals is one spoofing method. Spoofing techniques can also utilize the genuine broadcast signal. A simple example is relay spoofing or meaconing where the actual broadcast is received at one location and repeated at another. A more sophisticated version is to variably delay the components (signals from different transmitters) of actual broadcast and rebroadcast the signal to generate false ranges (“delay and relay” or selective delay). Another version is to modify the actual broadcast signal. Forms of direct injection attacks are similar to those of on-air spoofing attacks. They typically need a complicit or oblivious user as they require direct access to the receiver. Given this, they are simpler to implement than on-air attacks as the spoofed signals do not need to compete with the broadcast signals. Furthermore, the spoof “broadcast” is simpler to implement compared to its on-air brethren.
Several defenses against these attacks are possible. A physical defense is one possibility. Strong signal broadcasts represent a physical barrier against on-air attacks as the adversary needs to overcome the power of the genuine signal. This is one advantage of Loran. Another way to increase genuine signal power relative to an adversary is to use directional antennas. Another example of a physical barrier is tamper proofing. This may prevent injection attacks if the antenna and receiver represent one tamperproof unit.
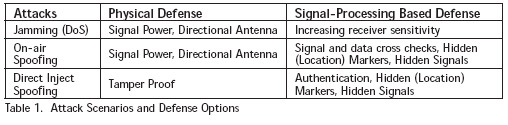
A second type of defense comes from signal design and authentication. Some features can be used to deter spoofing or cause on-air spoofing effects to be detectable depending on how it is conducted. One such feature is data authentication where the recipient can verify that the provenance of the information in the signal. Another method is hidden or location dependent marker. The technique provides information that is hidden in the signal that can only be known to the genuine source. The information is later revealed so verification is possible. A related technique is the use of location dependent marker. Another defense is hidden signal, an example of which is the GPS P(Y) code. If adversaries cannot determine the broadcast signal, then they cannot spoof it. Table 1 categorizes these attacks and potential defenses.
Loran Features for Security
There are many features of Loran that are useful in providing security to the signal. Foremost is its signal frequency and power. The Loran is a low frequency (LF) transmitted at a power level of 400 kW or more. At 100 kHz, the signal has a wavelength of three kilometers thus requiring a large antenna to transmit efficiently. Even a quarter wavelength antenna is physically difficult to realize. Thus, the most common Loran antenna in service is a 625 foot (190 m) top loaded monopole (TLM). Antennas as tall as 1350 feet (411.48 m) have been used. The high signal power, necessary to overcome atmospheric noise at long ranges, makes the signal more difficult to jam and spoof. These features make it difficult for adversaries to set up portable, inconspicuous, on-air attacks. Smaller antennas are significantly more inefficient.
eLoran will incorporate a data channel. The data channel utilizes pulse position modulation (PPM) to add data to the nominal Loran pulse. The data channel is designed to provide system information and differential Loran corrections. It can enhance security by providing authentication information to validate the data and source of the signal. A version of the authentication message system has been tested [9]. Furthermore, the data modulation itself can be useful in detecting on-air spoofing as discussed later.
Another difference between Loran and GNSS is that the former shares its frequency using time division multiple access (TDMA) while the later does it using code division multiple access (CDMA). That Loran is a pulsed broadcast also has security implications. This characteristics makes it more susceptible to “delay and relay” spoofing as signals from different stations are easily separated in time.
On-Air Attacks: Jamming & Spoofing
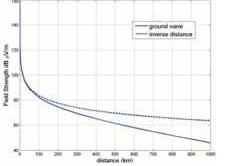
Jamming a signal involves overcoming the broadcast power of the signal. A general straight forward jamming broadcast is transmission of roughly equal received power at the carrier wave frequency. Due to distance, the received Loran power is significantly less than 400 kW radiated by the transmitter. The power falls off at greater than the nominal square of the distance due to attenuation for propagation along the ground [10]. This can be seen in Figure 1 which uses the nominal groundwave model from [11]. A 400 kW transmitter 300 kilometers away is received with roughly the equivalent power as a 40 W transmitter 5 km away. These are equivalent to a transmitter radiating 4 kW to a user 0.5 km away. The 300 km distance serves as a reasonable value for distance between a user and a close transmitter.
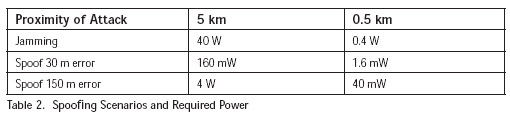
Spoofing a Loran signal by overcoming the transmitted signal is even more challenging than jamming. Part of the difficulty lies transmitting a Loran signal from a short, high Q, antenna. Short, high Q antennas have bandwidths that are much narrower than the signal bandwidth. Thus broadcasting a Loran signal from such antennas is more inefficient than transmitting a pure tone [12]. As a result, spoofing by broadcasting a tonal or near tone signals and affecting the measured time of arrival (TOA) is likely preferred it can be achieved with less power than that needed for jamming.
Antenna Model
The ability to radiate the power from a very short antenna is examined. A very short antenna is one whose height is much less than the transmitted wavelength. As the Loran wavelength is 3 km, even a 100 m antenna may be considered very short! Assuming a short monopole antenna on a perfect ground plane is used, the standard radiative resistance is given by Equation 1. If radiative resistance is the sole governing factor, then radiating the power levels in the previous section would only require currents on the order of ten amperes. However the reactance also be considered.

For a very short antenna, the reactance of the antenna is mostly capacitative. Equation 2 gives the reactance of a short monopole antenna where Δz is twice the antenna height (h) and a is the wire radius [13]. A similar result can be gained from empirical derivations. Equation 3 is the capacitance from a vertical wire of length h and diameter d with k being an empirical factor related the height above ground of the low point of the wire [14]. The reactance derived from Equation 3 is seen in Equation 4 and is essentially the same as Equation 2 for wires close to the ground (k ~ .44).
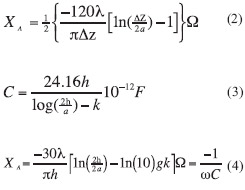
The voltage difference in a short antenna is effectively governed by the reactance. The current flow is simply the voltage difference divided by the magnitude of the impedance. This is given in Equation 5 where Rohmic (given in Equation 6) is the ohmic resistance (losses) in the antenna. For simplicity and conservativeness, this term is ignored.
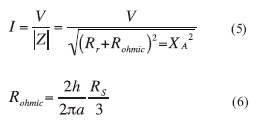
From the result, the radiated power can be calculated given an assumed voltage difference and an antenna radius. A reasonably conservative assumption for a maximum voltage potential is 45 kV. Results for an antenna radius of 5 cm at maximum voltages of 5, 25, and 45 kV are seen in Figure 2.
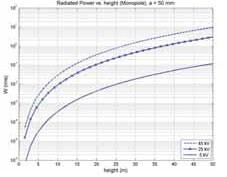
The results have some dependency on antenna radius with the general trend being radiated power increases with antenna diameter. Table 3 shows the antenna height needed to achieve the required radiated powers from the scenarios discussed for three different antenna radii.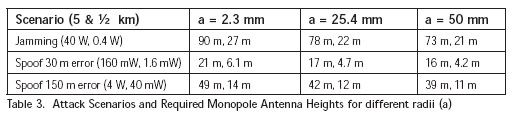
The analysis indicates that, unless an attacker is quite close, an on-air attack would require antenna structures that are quite significant – over 15 meters in the most optimistic case at 5 km. At ½ km, the antenna heights are more achievable but they will likely be noticed if they are at that distance to the user.
The analysis applies specifically to very short antennas and it does not consider other factors such as top loading which also improves performance. As antennas get larger, the reactance is lower than suggested by Equation 2 due to inductance. In fact, measurements of an operating Loran antenna show a reactance of -25 Ω, much less than calculated by the equation [12].
The analysis assumptions represent an optimistic case from the attacker’s perspective. It assumes away many losses such as ohmic and matching losses. It assumes no transmitter inefficiencies. It also assumes a perfect ground plane which an attacker is unlikely to approximate due to the amount of preparation needed to set this up.
Detecting On Air Spoofing
Spoofing can be detected on modulated Loran pulses especially if its effect is large. Spoofing as described previously, overlays the broadcast Loran signal with a tonal signal which alters the determined time of arrival (TOA). However, this form of attack leaves residuals that can be detected.
One detection method is to examine PPM pulses. Since the TOA of PPM pulses are not known a priori, the effect of the overlay cannot be predicted. Given tonal spoofing, the spoofer effects depend on the data symbol on carried by the PPM pulse. Hence, the spoofer cannot control the outcome. Using 9th pulse modulation as an example, spoofing a 300 m error will result in certain symbols being shifted by one while others will be unchanged as seen in Figure 3.
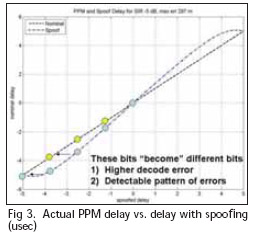
The spoofing is detectable since the symbol errors are systematic and occurs at a high rate. The discrepancy can be checked by the receiver by comparing its actual error rate to expected error rate. With cross checking of modulated pulses, the maximum range error that can be induced is about 250 m or less.
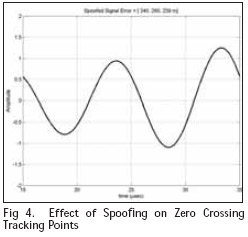
Spoofing also leave other traces on the signal that can be checked. One detection method is to examine multiple tracking point. A short monopole is narrowband and hence difficult to “instantaneously” turn on and off. As a result, spoofing will likely affect multiple Loran cycles. Even if the relative phase between a likely spoof signal and the Loran signal is maintained, the Loran signal envelope changes resulting in a different spoofed “error” at each tracking point. The deviation can be derived by both analysis and simulation. Figure 4 shows an example from simulation. In the figure, spoofing a 239 m error on the 30 microsec (sixth zero crossing) tracking point results in a 280 m error at the 25 microsec (5th zero crossing) and a 340 m error at the 20 microsec point.
Another means of spoof detection is the use of magnetic (H) field antennas. These antennas allow for the determination of received signal direction [15]. A single, on-air spoofing antenna can only generate signals from one direction. Hence a receiver designed to use an H field antenna will be able to distinguish the spoofer from the true system which would have signals coming from multiple directions. Furthermore, the receiver can check the consistency of the incoming signal directions with its calculated location.
Direct Injection Attacks
Resistance to on-air attacks is only one form of robustness. Direct injection attacks such as when the receiver is connected to a spoofing simulator also can pose a navigation security issue. Such an attack likely involves a complicit user with an incentive to deceive the navigation system. Examples include avoiding restricted zones or road toll charges. Such attacks circumvent the physical difficulties mentioned in the previous section. Other security features are necessary to mitigate such attacks. Two useful techniques for Loran to counter these attacks are: 1) authentication and 2) location dependent or hidden markers.
In the context of navigation, ideal authentication verifies the signal source and that the signal has not been maliciously delayed. The former may be provided by schemes based on data or source authentication techniques. Authenticated time dependent data reduces vulnerability to attacks where the signal is captured, stored and rebroadcasted. A symmetric key based data authentication protocol, Time Efficient Stream Losstolerant Authentication (TESLA), has been suggested for use in navigation [16] [17]. TESLA has been test implemented on Loran [9]. Another category of data authentication techniques that can be used is cryptographic signatures. Cryptographic signatures use a public-private key pair. They require distribution of a public key that is confirmed to be from the true system and a mechanism for revoking and redistributing public keys should a private key be compromised. While these systems require more processing (orders of magnitude) and longer keys than symmetric key systems, the gap can be narrowed with newer techniques such as those based on elliptic curves [18]. Both methods may be modified for eLoran and other low bandwidth navigation systems with some performance loss [19] [20].
Even with data authentication, the signal can still be delayed and quickly rebroadcast. Location dependent information and other hidden markers may be used to compliment data authentication and reduce the threat. For Loran, cross rate interference (CRI) provides one means. CRI cause different data bit errors depending on location. Receipt of the full message allows the Reed Solomon error correction to identify these interfered or “hidden” bits. Data authentication and time dependent data are needed so that a spoofer cannot generate a valid message a priori and the user can cross check the “freshness” of the message. The result is that a spoofer cannot generate the full sequence of data until after it receives the full message delaying its ability to rebroadcast. The delay from needing the full message and the time dependent information makes it difficult to trick users with reasonable knowledge of time. The weakness of CRI is that it has slow spatial decorrelation. The attacker can be several kilometers away and still experience the same CRI effects. It may be possible to augment the Loran broadcast specifically to improve the performance of the concept.
Conclusions
The article examines navigation security by using eLoran as a case study. It discusses the possible attacks that could affect the signal and user. It determines the vulnerability level and looks at available mitigations. I
n analyzing on-air attacks, the article quantifies the amount of power needed to jam or spoof Loran signals and determines the feasibility of an attacker to achieve these levels. While the required power is orders of magnitude larger than that need to jam GNSS, it is still not very large.
The difficulty in attacking Loran lies in generating the required radiated power from a short antenna. The analysis shows that generating a few milliwatts of output at low frequency on a small antenna requires significant input voltage. Hence, on-air jamming and spoofing is tremendously challenging and requires significant infrastructure to achieve. While certain forms of spoofing are easier, they still represent a significant challenge to an attacker. Even if the equipment issues can be overcome, spoofing effectiveness is limited in terms of the error inducible and detectability.
For direct injection attacks, the article examines potential defenses that are or could be incorporated into the system. It discusses techniques to aid the authentication of the Loran signal and its use with location based makers. These represent the major defense against direct injection attacks.
Disclaimer
The views expressed herein are those of the authors and are not to be construed as official or reflecting the views of the U.S. Coast Guard, Federal Aviation Administration, Department of Transportation or Department of Homeland Security or any other person or organization.
Acknowledgments
The authors gratefully acknowledge the support of the Federal Aviation Administration and Mitchell Narins under Cooperative Agreement 2000- G-028. They are grateful for the support their support of Loran and the activities of the LORIPP. The authors would also like to acknowledge Tim Hardy and John Pinks at Nautel.
Bibliography
“Vulnerability Assessment of the Transportation Infrastructure Relying on the Global Positioning System,” John A. Volpe National Transportation System Center, August 20, 2001.
Press Office, U.S. Department of Homeland Security, “Statement from DHS Press Secretary Laura Keehner on the Adoption of National Backup System to GPS,” February 7, 2008
General Lighthouse Authorities of the United Kingdom and Ireland, Research and Radionavigation, “The Case for eLoran,” Version 1.0, May 2006
Scott, L., “Anti-Spoofing & Authenticated Signal Architectures for Civil Navigation Systems”, Proceedings of the Institute of Navigation GPS Conference, Portland OR, Sept 2003
Kuhn, Mark us G., “An Asymmetric Security Mechanism for Navigation Signals”, 6th Information Hiding Workshop, 23-25 May 2004, Toronto, Canada, Proceedings, LNCS 3200, pp.239–252, Springer-Verlag.
Bowditch, Nathaniel, “Chapter 12: Loran”, The American Practical Navigator, Paradise Cay Publications, 2004
Forssell, Borje, “The Dangers of GPS/ GNSS”, Coordinates, February 2009
Humphrey, T. E., Ledvina, B. M., Psiaki, M. L., O’Hanlon, B. W., and Kintner, Jr., P. M., “Assessing the Spoofing Threat: Development of a Portable GPS Civilian Spoofer,” Proceedings of the Institute of Navigation GNSS Conference, Savannah, GA, Sept 2008
Qiu, Di, Lo, Sherman, Peterson, Benjamin, and Enge, Per, “Geoencryption Using Loran,” Proceedings of the Institute of Navigation National Technical Meeting, San Diego, CA, January 2007
International Radio Consultative Committee, “Ground-Wave Propagation Curves for Frequencies Between 10 kHz and 30 MHz”, CCIR Recommendation 368-7, Geneva last updated 1992.
Lo, Sherman and Enge, Per, “Analysis of the Enhanced LORAN Data Channel”, Proceedings of the 2nd International Symposium on Integration of LORAN-C/ Eurofix and EGNOS/Galileo, Bonn, Germany, February 2001, pp. 159-168
Hardy, T., “The Next Generation LF Transmitter Technology for (e)LORAN,” Proceedings of the Royal Institute of Navigation NAV08/International Loran Association 37th Annual Meeting, London, UK, October 2008
Stutzman, Warren L., Thiele, Gary A., Antenna Theory and Design, Second Edition, John Wiley & Sons, Inc, New York, 1998
Jordan, Ed ward C., Electronmagnetic waves and radiating systems, Second Edition, Prentice-Hall, Englewood Cliffs, NJ, 1968
Johannesse n, Erik, “Loran’s Role in Future PAT,” Proceedings of the 35th Annual Convention and Technical Symposium, Groton, CT, October 2006 (Presentation only)
Wullems, C ., Pozzobon, O., Kubik, K., “Signal Authentication and Integrity Schemes for Next Generation Global Navigation Satellite Systems,” Proceedings of the European Navigation Conference GNSS, Munich, July 2005
Perrig, A. Canetti, R., Tygar, J.D., and Song, D., “The TESLA Broadcast Authentication Protocol,” CryptoBytes, 5:2, Summer/Fall 2002, pp. 2-13
National Security Agency (NSA), The Case for Elliptic Curve Cryptography, 2009, http://www.nsa.gov/business/ programs/elliptic_curve.shtml
Becker, Georg, et. al., “Efficient authentication mechanisms: A Radio-navigation case study,” Proceedings of the Institute of Navigation GNSS Conference, Savannah, GA, September 2009
Lo, Sherman and Enge, Per, “Authenticating Aviation Augmentation System Broadcasts”, Proceedings of the Institute of Navigation/Institute of Electrical and Electronics Engineers Position Location and Navigation Symposium 2010, Indian Wells, CA May 2010
 |
|
|||||
 |
|
|||||
 |
|
My Coordinates |
EDITORIAL |
|
News |
INDUSTRY | GPS | GALILEO UPDATE | LBS | GIS | REMOTE SENSING |
|
Mark your calendar |
SEPTEMBER 2010 TO NOVEMBER 2011 |
Pages: 1 2











 (No Ratings Yet)
(No Ratings Yet)





Leave your response!