| GNSS | |
GNSS spoofing analysis by VIAS
A metric, Vulnerability Index Against Spoofing, is proposed and used to assess the effectiveness of a spoofer |
|
 |
|
||||
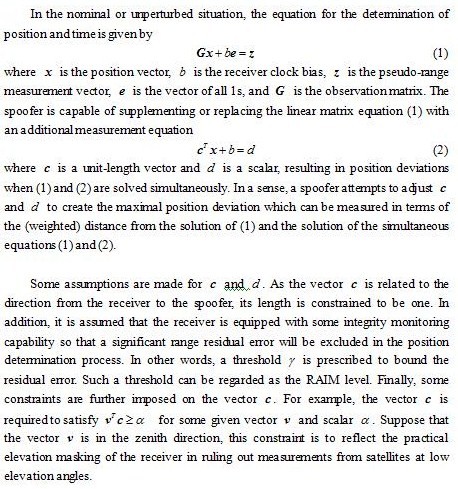
The GNSS (Global Navigation Satellite System) positioning is known to be vulnerable to interference due to the long distance of radio-signal travel and the resulting low signal power. In the presence of interferences or spoofing, the GNSS navigation performance is likely to be degraded and the navigation function may even be incapacitated. Throughout the years, many GNSS interference mitigation techniques have been developed. A challenge in GNSS interference mitigation is that a wide class of interferences needs to be considered. These interferences range from wide-band noises, narrow-band continuous-waves, frequency modulated interferences, pulsed-type interferences, to PRN (Pseudo Random Noise)-type interferences. Among these interferences, PRN-type interferences originating from pseudolites or re-radiators manifest themselves as GNSS-like signals, bearing the same frequency, format, and code modulation as legitimate GNSS signals. In some navigation applications, pseudolites can be used to enhance accuracy and availability. However, when these devices are used in an adverse manner, they may spoof GNSS receivers. In the celebrated report, it is stated that “A spoofer also can defeat nearly all anti-jamming equipment.” Existing mitigation methods against spoofers rely on verification of navigation messages, successive cancellation, and antenna array techniques.
Given that the PRN-type interferers or spoofers are difficult to detect and resist, it is of interest to assess the worst-case position/time deviation when a GNSS receiver is subject to hazardously misleading information from such kind of devices. Essentially in a radio-based navigation system, a set of transmitters broadcast ranging signals to the receiver for the latter to determine its position and time. A spoofer is to augment the existing system with a ranging measurement in a similar form with those of the navigation system so that the receiver will also utilize the augmented signal for position fix. As the augmented signal is subject to misleading information, the resulting navigation accuracy is affected and the navigation function may be denied.
Two types of spoofing techniques can be envisioned. One is to supplement the existing positioning equations with extra range/pseudo-range measurements. The supplement-type spoofing technique employs additional equations together with the original ones for the determination of position and time. Another type of spoofing techniques, which is referred to as the replacement-type technique, is to in-validate some existing measurement equations and replace them with others that are purposely created to alter the resulting position and time solutions. In general, the replacement-type technique may lead to more detrimental effect in GNSS positioning. One way to implement such a spoofer is to broadcast a PRN-like signal that have the same PRN number as that associated with the measurement equation. When the intentional PRN-like signal over-power the satellite signal, the receiver is likely to be forced to track the intentional signal and utilize the message for positioning. Fig. 1 depicts the acquisition diagram of such a scenario in which both the signals of a GPS satellite and a pseudolite are acquired. The two signals bear the same PRN. Yet, the one from the pseudolite is stronger than that from the satellite. Consequently, the receiver can be misled.
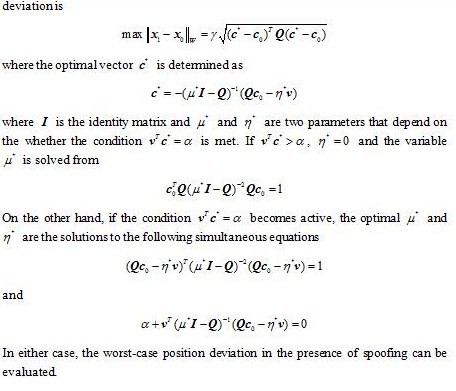
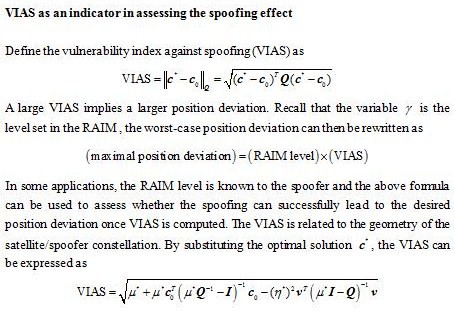
As spoofers may inject erroneous pseudorange measurements to the navigation receiver with false message, it is important to assess the spoofing effect on the resulting PVT solution. In the following, an optimization method is employed to determine the worst-case misleading message of a spoofer to make a GNSS receiver astray. It is shown that the worst-case position error can be expressed as a product of the range residual (or RAIM level) and a geometry-related factor. The geometry-related factor which is termed as the vulnerability index against spoofing (VIAS) reveals the geometric relationship between the GNSS constellation and the broadcast position of the spoofer in affecting the resulting position deviation. The analysis result is expected to be beneficial to the design of spoofers and anti-jam receivers. For the former, the analysis reveals the design of the misleading information in creating the maximal position deviation. For the latter, the maximal position deviation can be assessed and a scheme for the verification of navigation messages is envisioned to protect the receiver from spoofing. 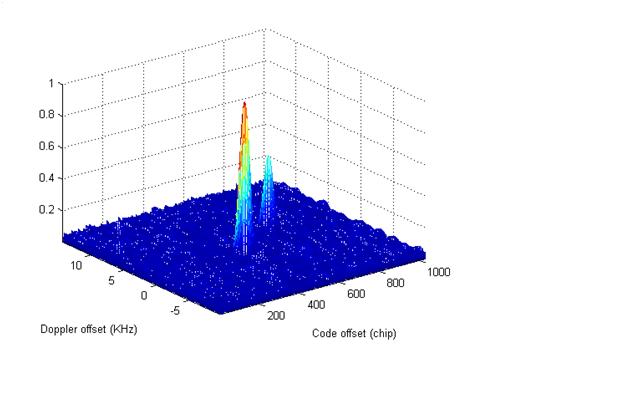
Fig 1. Two signals one (right) from GPS satellite and the other (left) from a pseudolite are acquired
Position Deviation Under Spoofing
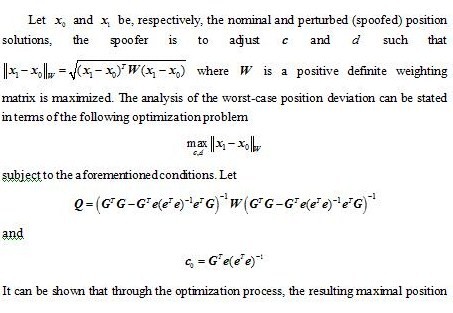
Recall that the objective is to assess how the GNSS position solution in the spoofed (perturbed) situation deviates from the unperturbed one. The analysis makes the following assumptions: (a) The spoofer is capable of adjusting its broadcast messages and timing offset. (b) The spoofer has a prior knowledge on the approximate location of the receiver. Also, information of the GNSS constellation is known to the spoofer. (c) The receiver is equipped with certain receiver autonomous integrity monitoring (RAIM) schemes so that a significant range domain residual is excluded. (d) The broadcast messages and ranging measurement of the spoofer are used in the receiver for position determination.
A well known formula in GNSS positioning is to characterize the RMS position estimation error in terms of the product of the standard deviation of the user equivalent range error and the dilution of precision (DOP). The DOP is related to the geometry of the GNSS constellation. Here, the maximal position error (in the deterministic sense) under spoofing is characterized in terms of the RAIM level and the VIAS. The RAIM level is allowable range residual error to meet the desired navigation task and the VIAS depicts the vulnerability of the geometry of the GNSS satellites in the constellation against the false reported position of a spoofer. Note that although the position deviation analysis is to account for the worst-case position error in the presence of spoofing, the design of can also be used in a homeland security type application. For example, it is possible to broadcast the spoofing information over a zone of security concern. In this case, any unauthorized GNSS receiver may then be subject to the spoofing and the consequential position deviation.
Simulation result
In the simulation, the location of Tainan, Taiwan is selected as the area of interest. Based on GPS almanac, the observation matrix can be computed. At any particular time instant, the distribution of the GPS satellites can be obtained and, henceforth, the worst-case vector that could potentially lead to a significant position error can be determined by solving the optimization problem. In the optimization problem, the elevation mask is set as 100 and the vector is along the local zenith direction. Fig. 2 depicts the VIAS for a period of twelve hour. The VIAS varies as a function of the distribution of observable satellites. At those instants when the VIAS is at its peak, the spoofer is more effective in creating a large position deviation. The PDOP is also illustrated in the figure. Not surprisingly, the VIAS is somehow correlated with the PDOP which means that when the satellite geometry is relatively good, it is more difficult to divert the positioning solution. 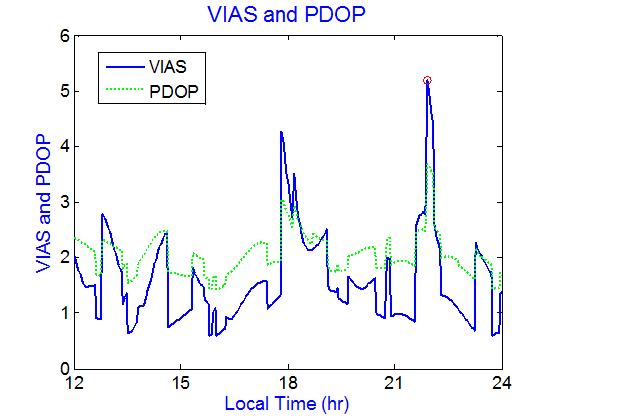
Fig 2 VIAS and PDOP
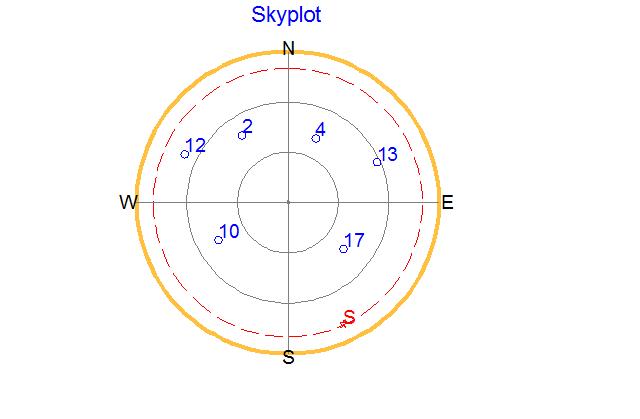
Within this period, the peak VIAS is 5.15 (marked by red circle in the figure) at around 22 o’clock. Fig. 3 depicts the GPS satellites/spoofer sky plot at this time instant. In this figure, six satellites are observable which are marked by blue circles with PRNs 2, 4, 10, 12, 14, and 17, respectively. The spoofer broadcasts its false position vector at the location as marked by the red pentagon symbol (S letter) in the figure. The spoofer reports its false position vector at a low elevation angle in an attempt to shift the balance of satellite distribution.
Fig 3 Sky plot of the GPS satellites and spoofer
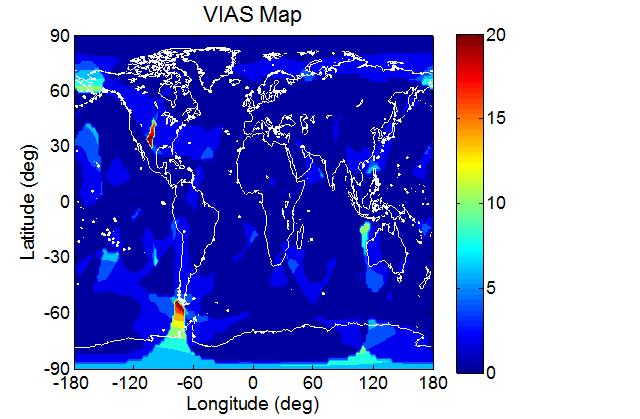
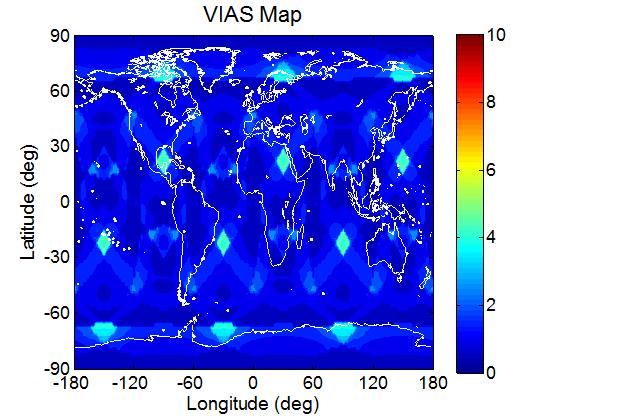
To see how the VIAS varies at different locations on the Earth, the VIAS map at the aforementioned time instant is presented in Fig 4. At some locations, the VIAS is very large (~20) which implies that the area is susceptible to spoofing. In the figure, the maximal VIAS occurs at longitude -78 and latitude -54.
Fig 4 VIAS map (GPS constellation)
Since the VIAS map is related to the GNSS constellation, the VIAS analysis approach is applied to the Galileo constellation to assess the susceptibility of the system against spoofing. In this analysis, the 30-satellite Galileo constellation is used. The result is depicted in Fig. 5. Since the Galileo constellation is a Walker constellation, the distribution is more uniform and the worst-case position deviation (assuming the same RAIM level) due to spoofing is not as severe as in the GPS case. In the Galileo case, the maximal VIAS is 5.16. However, the maximal value occurs at several different locations.
Fig 6 VIAS map (Galileo constellation)
Summary
The GNSS position deviation effect under spoofing is analyzed. A metric, VIAS, is proposed and used to assess the effectiveness of a spoofer. It is shown that the worst-case position deviation in the presence of spoofing can be expressed as the product of the VIAS and a term relating to range residual or RAIM level. The use of VIAS is of benefit in assessing the use of GNSS navigation in resisting spoofing. The VIAS which depends on both time and location may also shed light on the design of a robust GNSS constellation. The analysis also suggests a method to mitigate the spoofing effect in affecting navigation accuracy. To protect the GNSS receiver from the contamination of spoofing messages, the receiver can employ a scheme to rule out or de-weight signals originating from the worst-case direction . In addition, as the worst-case reported position of a spoofer tends to be at low elevations, an elevation-dependent weighting in determining the navigation solution can somehow relax the limitation.
Acknowledgements
The research was supported by the National Science Council, Taiwan under grant NSC 98-2221-E-006-194-MY3.
References
1. Spilker, J. J. Jr. and F. D. Natali, F. D. (1996). Interference Effects and Mitigation Techniques. B. W. Parkinson et al (eds.) Global Positioning System: Theory and Applications, Vol. I, American Institute of Aeronautics and Astronautics, 717-772.
2. Ward, P. (1996). Effects of RF Interference on GPS Satellite Signal Receiver Tracking. E. D. Kaplan (ed.) Understanding GPS: Principles and Applications, Artech House, 209-236.
3. Juang, J. C., Cheng, K. Y., Tseng, C. L., and Lo, C. F. (2004). The Design and Test of a Dual-Frequency GPS Pseudo-Satellite Augmentation System. Proc. Int. Conf. on Integrated Navigation Systems.
4. Volpe National Transportation Systems Center. (2001). Vulnerability Assessment of the Transportation Infrastructure Replying on the Global Positioning System.
5. Juang, J. C., Chang, C. L., and Tsai, Y. L., (2004). An Interference Mitigation Approach Against Pseudolite. Proc. Int. Sym. on GNSS/GPS.
6. Juang J. C., and Chang, C. L. (2005). Performance Analysis of GPS Pseudolite Interference Mitigation Using Adaptive Spatial Beamforming. Proc. ION Annual Meeting.
My Coordinates |
EDITORIAL |
|
Mark your calendar |
FEBRUARY 2011 TO NOVEMBER 2011 |
|
News |
INDUSTRY | LBS | GPS | GIS | REMOTE SENSING | GALILEO UPDATE |












 (5 votes, average: 3.20 out of 5)
(5 votes, average: 3.20 out of 5)





Leave your response!