| Applications | |
Cryptographic digital technology for the prevention of property theft
Using cryptographic digital technology, a mobile application could be developed to eliminate property registry fraud even before it occurs |
 |
|
Abstract
Property registry fraud is a form of identity theft used to steal property by forging documents in the name of the property’s rightful owner. Property registry fraud impacts land rights across the globe and, in the United States, is a crime that commonly affects the most vulnerable: the elderly and families of the recently deceased. Many times, property registry fraud is not detected until irreparable harm has been done. The costs of this crime are economic, social and judicial. Using cryptographic digital technology, a mobile application could be developed to eliminate property registry fraud even before it occurs. In deploying such an application, developing countries could leapfrog the capabilities of more technologically advanced governments in securing the property ownership of individuals and prevent property registry fraud from occurring, thereby protecting the land rights of the most vulnerable people.
Introduction
Property registry fraud is a form of identity theft used to steal property by forging and recording documents in the name of the property’s rightful owner. As stated in a consumer report from the California Department of Real Estate:
the county recorder is not responsible for verifying the validity, authenticity or legitimacy of the document that is recorded. In other words, the recorder is not responsible for detecting a fraudulent document, and the recorder does not look beyond the document itself. If the document meets the essential recording requirements, and the proper fees are submitted, the county recorder is obligated to and will record the document. (Bell & Bakotich, 2012)
A news article published by the United States Federal Bureau of Investigation details a number of ways this type of fraud can be perpetrated (The Federal Bureau of Investigation, 2008). A South African news article details the theft of a widow’s home (Barbeau, 2015). Between 2015 and 2018 property registry fraud cases totaled over $112 million in impacted property in New York City alone (The Grand Jury of the Supreme Court of the State of New York County of New York, 2019). It commonly also impacts the most vulnerable: the elderly, medically disabled and families of the recently deceased. In case after case, families have lost properties representing the whole of their accumulated wealth and history (The Grand Jury of the Supreme Court of the State of New York County of New York, 2019). Property registry fraud is an expensive and ubiquitous problem that impacts countries across the globe.
Current government agencies including the New York Department of Finance (NYC Department of Finance, 2019) and the United Kingdom Land Registry (HM Land Registry, 2019) recommend a variety of property registry fraud security measures to make property owners less vulnerable including: make the property look maintained and cared for, sign up for alerts to all changes in recorded documents in relationship to owned property, and to report any fraudulent activity immediately to the sheriff’s office.
Unfortunately, the global status quo involves catching perpetrators after the fact, sometimes after irreparable financial harm has been done (Frost, 2019). In deploying preventive technologies, developing countries could leapfrog the current state of affairs in developed countries and provide more secure land ownership for all citizens.
The web enabled digital advancements of the past decade have made property registry fraud more likely to be profitable without detection. Property thieves have the ability to correlate data from many sources to identify vulnerable properties. A thief can correlate death records with property data from a variety of sources to find properties owned by the recently deceased. In this case, a forged property transfer document can be less likely to be detected before the thief is able to profit. The speed and global nature of modern digital finance in the ability to get a loan with the stolen property as collateral, or for the thief to sell the property outright make realizing profit and disappearing with the funds even easier. Our current methods of registering and recording property records were not designed with these realities in mind. While they may have been sufficient for a pre-digital world where the pace of finance was slower and real estate transactions were more localized; in our modern world they represent a significant security vulnerability. The fraud resistant conveyance of property requires secure verification of all parties at the time of notarization and at the time of recording.
Public key cryptography
Public key (commonly known as RSA) cryptography involves the generation of public/private key pairs. The private key is known only to the owner, while the public key is disseminated to anyone that the private keys owner would like to communicate securely. RSA key pairs are widely used, trustable, and form the basis for nearly all secure online services (Rivest, Shamir, & Adleman, 2019). Beyond its role in our daily lives in e-commerce and online banking (Tip Top Security, 2017), RSA key pairs can serve as a basis for preventing the creation and recording of fraudulent documents.
Public/private key pairs can be used to digitally sign information in such a way as to securely tie the owner of the private key to the signed artifact. A holder of the public key can verify that a digital signature represents the information that was provided. The public key holder can also verify that a specific private key holder was the signer, making the digital signature and the associated information impossible to forge by another party.
Public Key Infrastructure (PKI) refers to a centralized collection of public keys from known users of known identities. A type of PKI managed by certificate authorities secures all internet traffic via the SSL protocol (Russel, 2019). PKI can eliminate fraud by allowing digital documents to be created and signed in a way that guarantees that the signer of a document is who they purport to be. Paperless land transfer systems of unprecedented efficiency can be built by recording these digital documents to a blockchain based public registry.
A paperless land title transfer system was designed by Medici Land Governance1 to facilitate streamlined communication with government agencies in Rwanda.
The system was designed to allow a notary to securely identify a buyer and seller and then digitally sign the transfer agreement with PKI private keys. This creates a secure digital transaction of the transfer through a government agency on to a blockchain. This paperless transfer of land titles, secure registration of ownership and the elimination of the requirement to visit a land office prevents three main failings in the land registry today.
1. The double selling of land.
2. The impersonation of a seller.
3. Independent verification of land titles.
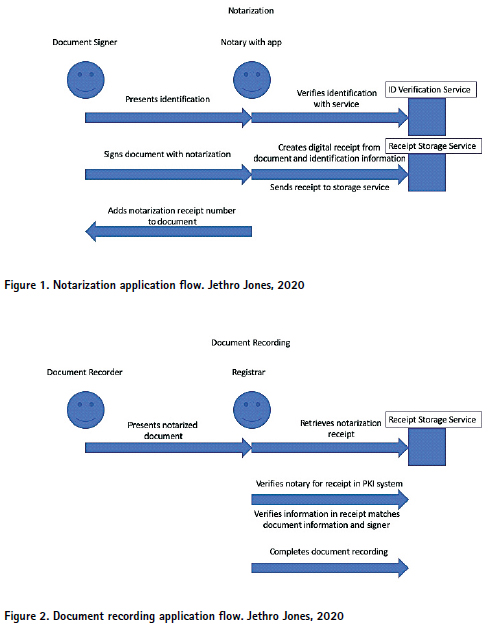
The system demonstrates a substantial increase in security, ease of use and efficiency together with automatic transfer of title. In the absence of universal Public Key Infrastructure, which is the current situation in nearly all countries, a PKI system for notaries could be used to improve the security of the creation and public recording of property records, significantly lowering the risk of fraud. A mobile application could be developed to enable notaries both to securely identify an individual and to securely capture the key elements of a notarized document in a fraud proof way.
To securely identify an individual at the time of document signing, the notarization application would verify identity by matching the name, ID number, and even government issued identification card photos with a centralized service.
The mobile application would also hold a private key for the notary with the public key recorded with the notary PKI system. A cryptographically signed digital receipt of the document notarization would be created and stored with a centralized service for reference when the physical documents are officially recorded with the registrar. When the physical document is notarized, crucial information about that document would be captured, digitally signed and centrally stored for later reference. This would include the date and time provided by the signing device, the names of parties involved along with identifying information (state ID number) and a short note about the nature of the document, i.e., a named party conveys a given property to another named party. The date, along with a short unique identifier to cross reference with the centrally stored digital receipt, would be written on the physical document being notarized along with the official stamp.
At the time of recording, the registrar would pull up the digitally signed and centrally stored receipt of this notarized document for cross referencing all information: date, parties involved and intent.
The key benefits to this system are that it becomes impossible to forge the notarization of a document because the key information and the notarization itself are signed in a cryptographically secure and tamper-proof way by a notary who is securely and uniquely identifiable in the PKI system. The digitally signed record is stored in a central service as a receipt for later reference. A secure chain is created from the moment of notarization to the time of recording that makes the forging of notarized property transfer documents extremely difficult. This makes it significantly harder, if not impossible, to record fraudulent documents at an official registrar.
Decentralized Public Key Infrastructure
A suite of new technologies in the cryptographic space provides additional opportunities to extend these ideas and create more robust systems with even greater efficiency, security, convenience and workflows with greater complexity. Decentralized Public Key Infrastructure (DPKI) refers to the suite of technologies that do not rely on a centralized authority for the management and security of keys which is part of current PKI systems used by certificate authorities. In a DPKI system public keys are stored on a public blockchain or distributed ledger and can be created, updated and revoked at will. This lowers cost and adds flexibility and capability (The Sovrin Foundation, 2018). The two most prominent DPKI systems are uPort and Sovrin.
Decentralized identity
Decentralized identifier (DID) refers to a public key addressing system, and is a standard coming from the W3C. It includes the public key as well as routing information to communicate directly with the holder of the associated private key. DIDs can be exchanged in a peer to peer fashion for encrypted communication and document exchange. DIDs can also be published to a public blockchain forming the basis of DPKI. With a DID publicly accessible and associated to a specific authorized identity any signed artifacts for that key pair can be publicly verified without reliance on a centralized authority. As stated by the Sovrin foundation: DIDs are the first globally unique verifiable identifiers that require no registration authority… DIDs enable true self-sovereign identitylifetime portable digital identity for any person, organization, or thing that can never be taken away. (The Sovrin Foundation, 2018)
The DID can be included in the signed artifact itself, creating a very straightforward verification method with the associated DID, including the public key published to the blockchain.
Verifiable credentials (VC)
In the Sovrin system, a verifiable claim, also known as a verifiable credential, is defined as:
a piece of information that is cryptographically trustworthy. In Sovrin,a verifiable claim is shared as a proof and is anchored to the public ledger by a credential definition and public DID written by the credential issuer. Typically, this proof is in the form of a digital signature. A Sovrin Verifiable Claim may be verified by a public key associated with the Issuer’s DID. An example of a verifiable claim could be a digitally issued driver’s license. (The Sovrin Foundation, 2018)
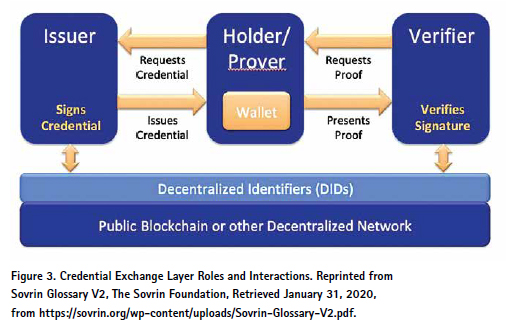
The use of verifiable claims involves a triangle of trust. Every verifiable claim has a claim issuer (the entity that issues a claim to a holder), the holder (the user keeps the credential in a digital wallet on a personally held mobile device), and potential verifiers who would request some digital proof from the holder which can be satisfied by the verifiable claim.
There are two additional artifacts published to a blockchain which include the schema definition and credential definition. The schema definition is a machine-readable artifact that allows for interoperability. An example could be a passport schema definition which could include full name, birthdate, and country of origin.
The credential definition is a specific instance of a schema definition associated with a single issuer. A single national government could publish a credential definition which references the generic passport schema definition. Any digital passports issued as verifiable credentials would reference the published credential definition which would in turn reference the specific schema definition. In this case the issuing national government would be the credential issuer and the individual receiving the passport would be the credential holder. The credential issuer would have a publicly registered DID published to a blockchain.
When the time comes for an individual to use their digital passport, they would receive a digital verification request from the credential verifier. This could be the passport officer at a port of entry. The verification process includes verifying that the credential was digitally signed by the issuing government and matches the blockchain DID. This is the digital identity of the national government and includes the public key, which as previously demonstrated proves identity and authority. The verifier would also reference the published schema definition and credential definition to validate all information required. At this point in the process, additional verifiable credentials could be issued to the holder which would be analogous to entry/ exit stamps in a passport book or visa which would expire at a certain point in time (The Sovrin Foundation, 2018).
Let’s now look at another real-world example: The Department of Motor Vehicles (DMV), a licensee and a police officer. All parties will have DID capable wallets. The DMV would issue a driver license verifiable credential to a licensee which would be held in their digital wallet. This would contain the licensee’s necessary information: age, driver’s, license number, whether their license is valid, and if they are allowed to drive. This data is also cryptographically signed by the DMV’s private key. The corresponding public key is published to a public ledger.
If a police officer pulls the licensee over while the licensee is driving, the officer would use a device to verify the verifiable credential held by the licensee, verify that is what signed by the DMV and that the licensee is able to drive.
Strong Identification or validated identification refers to a DID which is connected to a real-world identity through a credential issued by a trusted authority. This could be a driver license, passport, or a digital credential issued by a notary after reviewing the credential holders physical identifying documents. These ideas can be extended to building land administration systems and processes. From our previous examples using private keys and traditional PKI, we can build a system using DPKI, DIDS and verifiable credentials. Using a verifiable credential to prove identity allows for removing the identification verification step from notarization and possibly removing the notarization step entirely. With a secure identity credential issued by an appropriate government authority, we get the same fraud resistant guarantees in our previous system. It is guaranteed that the signer is who they claim to be. With this digital infrastructure in place and DPKI that extends to all users in the system, paper documents can be eliminated entirely. A digital purchase agreement can be created in an application that is digitally signed by the buyer and the seller. The identity credentials from all users become part of the secure workflow. Because there is no dependency on a paper-based agreement, the digitally signed purchase agreement can be instantly transferred to the government registrar for recording. Any other required steps, such as guarantees of clear title and mortgage origination, can be handled through verifiable credentials as well. For example, if a buyer needs to prove employment, a verifiable credential could be issued by their employer or to prove available funds, a verifiable credential could be issued by the bank. After recording a verifiable credential could be issued to the new buyer to be held in a mobile wallet to prove ownership with the government registrar as the issuer.
With these tools and infrastructure, bureaucratic workflows of unlimited complexity can be built that are orders of magnitude more secure and efficient than the paper-based processes that are the current status quo. Significant savings will be realized by landowners and governments by eliminating property registry fraud and other forms of document fraud before they can happen. This includes the economic and social cost of the fraud itself and the savings in not having to litigate and prosecute such cases in the justice system. In deploying such applications, developing countries could leapfrog the capabilities of more technologically advanced governments in securing the property ownership of individuals and prevent property registry fraud from occurring, thereby protecting the land rights of the most vulnerable people.
Endnote
1Medici Land Governance was established as a public benefit corporation to use advanced technology including blockchain to improve trust in information and institutions while helping individuals secure their land rights and improve their economic situation.
References
Barbeau, N. (2015). Widow’s Home Stolen. Retrieved from IOL:News that Connects South Africans: https:// www.iol.co.za/dailynews/news/ widows-home-stolen-1876257
Bell, W. S., & Bakotich, S. B. (2012). CONSUMER ALERT: What Should You Do If You Learn that a Forged and/or Fraudulent Deed Has Been Recorded Against Your Real Property? Retrieved from California Department of Real Estate: http://www.dre.ca.gov/ files/pdf/ca/2012/ConsumerAlert_ ForgedFraudulentDeeds.pdf
Frost, M. (2019). Relief could be coming soon for victims of deed theft. Retrieved from Brooklyn Daily Eagle: https://brooklyneagle.com/ articles/2019/04/08/relief-could-becoming- soon-for-victims-of-deed-theft/
HM Land Registry. (2019). Property Alert Service. Retrieved from HM Land Registry: https:// propertyalert.landregistry.gov.uk
NYC Department of Finance. (2019). Protect Your Property from Deed Fraud. Retrieved from NYC Department of Finance: https://www1.nyc.gov/ site/finance/taxes/deed-fraud.page
Rivest, R., Shamir, A., & Adleman, L. (2019). A Method for Obtaining Digital Signatures and Public-key Cryptosystems. Retrieved from MIT Computer and Artificial Intelligence Lab: https://people. csail.mit.edu/rivest/Rsapaper.pdf
Russel, A. (2019). What is a Certificate Authority (CA)? Retrieved from ssl. com: https://www.ssl.com/faqs/ what-is-a-certificate-authority/
The Federal Bureau of Investigation. (2008, 03 25). House Stealing. Retrieved from The FBI: https://archives.fbi. gov/archives/news/stories/2008/ march/housestealing_032508
The Grand Jury of the Supreme Court of the State of New York County of New York. (2019). Deed Fraud Grand Jury Report. Retrieved from Manhattan District Attorneys Office: https://www.manhattanda. org/wp-content/uploads/2018/12/ Deed-Fraud-Grand-Jury-Report.pdf
The Sovrin Foundation. (2018). Sovrin: What Goes on the Ledger? Retrieved from The Sovrin Foundation: https:// sovrin.org/wp-content/uploads/2018/10/ What-Goes-On-The-Ledger.pdf
The Sovrin Foundation. (2018). Sovrin™: A Protocol and Token for SelfSovereign Identity and Decentralized Trust. Retrieved from The Sovrin Foundation: https:// sovrin.org/wp-content/uploads/Sovrin- Protocol-and-Token-White-Paper.pdf
The Sovrin Foundation. (2018, December 8). What is a Verifiable Claim? Retrieved from The Sovrin Foundation: https:// sovrin.org/faq/what-is-a-verifiable-claim/
Tip Top Security. (2017). How Does HTTPS Work? RSA Encryption Explained. Retrieved from Tip Top Security: https:// tiptopsecurity.com/how-does-httpswork- rsa-encryption-explained/
The paper was prepared for presentation at the “2020 World Bank Conference on Land and Poverty”, The World Bank – Washington DC, March 16-20, 2020. Copyright 2020 by author(s).













 (3 votes, average: 1.00 out of 5)
(3 votes, average: 1.00 out of 5)



Leave your response!