| GNSS | |
So you think you are safe
About (mis)perceptions, unwarranted assumptions and unintended capabilities |
 |
|
When looking at the timeline of technology of today’s consumer electronics, there are several interesting connections with technology and associated infrastructure originally (at least partly) developed in the cont ext of DoD funded projects. Large-scale integration of this technology into consumer electronics created an economy of scale that is unmatched, enabling capabilities and services that otherwise may have been prohibitive due to cost. Besides being used in consumer electronics from a perspective of economic necessity, society has become strongly dependent on the continuous availability of the associated infrastructure. Although twenty years ago potential vulnerabilities were deemed as unrealistic, today we know different, and some of the lessons learned have been very expensive.
Except perhaps for the last statement, this discussion could have been about the GPS infrastructure made up by satellites, and the GPS receiver technology used in a wide variety of products with the information used for a wide variety of services (Certain applications only use the timing information). However, the discussion concerned the information infrastructure commonly referred to as the ‘Internet’ and the technology to access and transfer data and to manage and coordinate transactions. An important commonality between the two domains is the requirement that the data used is not interfered with. This article discusses the reliance on the technology and infrastructure from a safety perspective, and identifies trends that could contribute to a reduction in safety.
It is likely that when asked, most people will confirm that safety is important. However, when asked to define safety, it is unlikely that a single definition will result. To obtain a workable and acceptable definition for the purpose of the discussion in this article, some definitions are reviewed. The first one (source Wikipedia) is: ‘The condition of being protected against Physical, Social, Spiritual, Financial, Political, Emotional, Occupational, Psychological, Educational or other types or consequences of: Failure, Damage, Error, Accident, Harm, or any other event which could be considered non-desirable’. Many of the causes of unsafety mentioned in this definition are related to one another: A design error can result in a fault that leads to a failure. A resulting accident can cause damage and harm (which can have a physical nature, but also financial, political and psychological). Important to notice is that victims may never have felt ‘unsafe’ until the harm occurred. The safety referred to in this latter context is a perception (The perceived or subjective safety, which refers to the users’ level of comfort and perception of risk, typically does not consider standards or safety history. If such a perception is unwarranted, safety is an illusion).
A more engineering oriented definition of safety is: The control of recognized hazards to achieve an acceptable level of risk (In this context, risk is defined as ‘The probability of something happening multiplied by the resulting cost if it does’). Key in this definition is that safety requires awareness of vulnerabilities and the specification of their acceptability. To prevent an (unjustified) illusion of safety, awareness of all hazards, threats (A threat is a method of triggering a risk event) and vulnerabilities is required. In response to the identified risk, several types of mitigation can be pursued. Engineering and regulation are two of the most common.
Information integrity and continuity
Both communication and navigation rely on information. In the communication domain, safety is addressed through information security, comprising confidentiality, integrity, and availability. Safe navigation relies on continuity in the accuracy and integrity of the position data. Safe navigation also relies on traffic management, in which the surveillance function has to provide position data of all traffic, with high accuracy and integrity. Clearly, information integrity and continuity is critical for aviation safety. In the Required Navigation Performance (RNP) concept [1, 2, 3], the target level of safety is achieved by specifying performance in terms of accuracy, integrity, availability and continuity. Future Concepts of Operation (ConOps) developed under SESAR [4] and Nextgen [5] programs foresee an increased reliance on GNSS-based position estimation, both for aircraft navigation function and for the surveillance function. When considering operations that are specifically enabled by the GNSS, the possible causes and effects of a loss of integrity and continuity on safety need to be identified and analyzed. Based on the outcome, mitigation strategies and/or back-up systems may need to be designed and put in place.
Vulnerabilities
Both in the communication and navigation domain, security (Security: The degree of resistance to, or protection from, harm) vulnerabilities exist that threaten the information continuity and integrity. On the Internet, so-called Distributed Denial of Service (DDoS) attacks can disrupt information availability, while IPspoofing-based Man-in-the-Middle (MitM) attacks threaten information integrity. The timeline in Figure 1 illustrates how these threats evolved over the past 20 years.
As early as 1989, a vulnerability due to the possible sequence prediction in the transmission control protocol was discussed [6]. Although deemed unlikely by the experts at that time, 5 years later this vulnerability was exploited by Kevin Mitnick to break in to Tsutomu Shimomura’s computers in San Diego. Due to several books and reports written about this breakin [7], it serves as a useful warning that the barriers that need to be overcome to exploit vulnerabilities in a system are not cast in stone. Once a vulnerability is known, more and different means to exploit it are likely to be developed. As a result, the original assessment of the likelihood that a particular vulnerability will be exploited may lose its validity. This applies equally well to GPS vulnerabilities, and should always be considered, especially in case safety depends on it. To prevent an unjustified perception of security, any (expert) assessment that a particular vulnerability does not pose a threat should be accompanied with a wellsupported rationale that both identifies the underlying assumptions and indicates how their validity may change in the future.
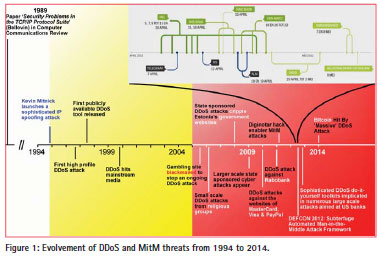
Whereas, IP-spoofing as performed by Mitnick required considerable expertise, the proliferation of DDoS tools on the Internet (which started around 1997) provided anyone with an incentive the capability to harass a particular website by overloading it with requests. Although at the end of the Nineties of the previous century such events were still rather limited, their amount (and bandwidth) and their targets increased tremendously during the following decade. In the Netherlands alone, in 2014, the website of every major bank, most newspaper sites, websites from railways and airlines and several government websites suffered DDoS attacks.
In the navigation domain, the equivalent to a DDoS attack is jamming. Although fifteen years ago it was concluded that ‘there is no credible spoofing threat and jamming threats can be managed’ [8], the timeline in Figure 2 illustrates how the jamming threat has evolved during over the past 20 years:
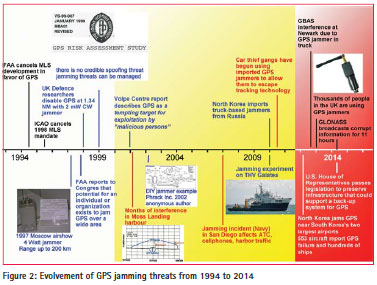
In 1994, motivated by promising demonstrations using GPS to provide landing guidance, the Federal Aviation Administration (FAA) cancelled further development of the Microwave Landing System (MLS), which until then was the intended replacement of the Instrument Landing System (ILS). In 1995, the International Civil Aviation Organization (ICAO) followed by cancelling its mandate that in 1998 ILS should have been replaced by MLS. The underlying rationale was that GPS would soon provide the same capability at a much lower cost. To assess the risk of using GPS for landing guidance, a thorough analysis was performed by the Applied Physics Laboratory of John Hopkins University. Based on the requirements in [9], the analysis used a classification matrix in which five levels of likelihood of the identified potential disturbance (Both intentional and unintentional disturbances) related failures (rows) and five levels of their impact on safety (columns) provide a total of 25 possible combinations (Figure 3).
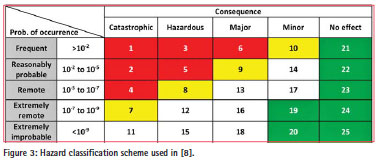
From a safety perspective, certain combinations of likelihood and impact are unacceptable (red cells 1-6 in the figure), whereas others were classified as undesirable (yellow), as acceptable but with FAA review required (white) or as acceptable (green cells). The study clearly identified that the potential for jamming existed, but at that time no combinations of likelihood and consequences for cells 1 to 6 were identified. After the 1999 risk assessment study, various other studies investigated the potential jamming and spoofing threats with varying assumptions about likelihood and impact of the threat [10]. Nowadays, due to the vastly increased amount of services relying on GPS and the vastly increased amount of jammers many of the early assumptions are no longer valid.
Regarding the intended replacement of ILS with GPS around the year 2000 (which was the basis for the cancellation of the MLS mandate), after more than $200 million in development effort, the FAA stopped further expenditures on the GPS Cat. 1 LAAS in January 2004. The good news is that ILS still provides safe landing guidance. The bad news is that the intended capabilities that a replacement system was to offer, such as curved and steep approach guidance to fl y noise abatement procedures, are not possible with ILS.
Although already in 2002 the hacker magazine Phrack published a schematic and software for a DIY GPS jammer, it still took some time for GPS jammers to reach a ‘consumer electronics’ level. Nowadays, they are offered on various websites, often with a ‘privacy incentive’. In spite of the fact that sale, use or possession is forbidden in many countries, legislation alone may prove not to be enough. Similar to the tools needed to launch a DDoS attack on the Internet, GPS jammers are available to everyone with an incentive to do so. It is reported that in the UK alone, thousands of people are using GPS jammers, and near airports multiple jamming events per day have been detected.
Spoofing: Navigation warfare meets Cyber
On the Internet, tools to cause considerable mischief by means of DDoS attacks have been available for over 15 years. More recently, sophisticated tools to ‘explore’ Man-in-the-Middle attacks have emerged. Cybersecurity is the container term used for activities related to dealing with these threats in order to protect information confidentiality, integrity and availability. Two important techniques to achieve cybersecurity comprise encryption and authentication. The lack of encryption in the civil GPS signal makes it particularly vulnerable to spoofing. However, compared to a MitM attack on the Internet, GPS spoofing requires a signal to be generated and synchronized with the actual signal before the spoofing can take effect. In research this is typically done by using a GPS signal simulator. An example is the research addressing questions concerning the required precision of the attacker’s spoofing signals [11].
With typical prices for a GPS signal simulator above 100k$, the spoofing threat may seem unlikely to happen. However, here too the barriers to be passed are reducing. Already in 2003, Logan Scott [12] warned that ‘rapid advances in computing power are making an all software implementation much more feasible’, followed by the warning that at some time in the future, ‘script kiddies using software downloaded from the Internet may mount a spoofing attack’. It does not seem to have happened yet, and one might argue that this is unlikely to become a serious threat, but the same could be said about software to manufacture a gun. The latter will only become a hazard if the person planning mischief not only has Internet access but also a 3D-printer. Whereas in [12] the ‘all software implementation’ was still a prediction, five years ago it was demonstrated that such a spoofer can be realized using an existing software-defined receiver with some extensions [13]. Since that time, various demonstrations have proven technical feasibility of a portable, low-cost, software defined spoofer.
The fact that it still may take some years for the spoofing threat to materialize can be regarded as temporarily good news for the nautical and aeronautical navigation functions relying on the position data, and for the power grids and secure financial transactions that depend on accurate timing information. However, for the GNSS-based surveillance function relying on Automatic Dependent Surveillance Broadcast (ADS-B), there is another threat on the horizon: Like the civil GPS signal, the ADS-B messages that are broadcast by an aircraft are unencrypted. The associated potential vulnerability did not go by unnoticed in the hacker community. In 2007, at the DefCon Hackers conference, it was suggested that ‘one could easily fake an ADS-B transmission’ [14]. To prove the feasibility, an ADS-B out application was designed and implemented on GNU-radio [15], and in 2012 it was indicated that the ‘plan is to release the software’, which could lead to a scenario similar to the one predicted in [12]. That same year, at the industry-sponsored Black Hat Security conference, another presentation about ADS-B spoofing using a software defined radio setup was presented. The paper [16] describes the hardware and software to generate ADS-B targets, and concludes that the potential for Denial of Service on ATC fl ight-space resource and ADS-B IN aircraft exists. For IT specialists, the following assessment of ADS-B security made at the 2012 Black Hat security conference may be particularly insightful: ADS-B is almost like “ALL R/W with ‘Guest as Admin’ enabled”.
To stimulate discussions that lead to a better awareness of the potential security/ safety implications, in [17] an overview of and classification of possible attacks on ADS-B is provided. In 2013, researchers from the University of Kaiserslautern in Germany, Armasuisse in Switzerland and the University of Oxford concluded that: ‘attacks on ADS-B can be inexpensive and highly successful’ followed by the conclusion that ‘any safety-critical air traffic decision process should not rely exclusively on the ADS-B system’ [18]. In follow-on research that analyzed current approaches to deal with this issue [19], it is concluded that ‘solutions currently under consideration (and in use in practice such as multi-lateration) can only be a fill-in, providing a quick improvement to the security of the current system’.
The timeline in Figure 4 provides an overview of spoofing-related developments.
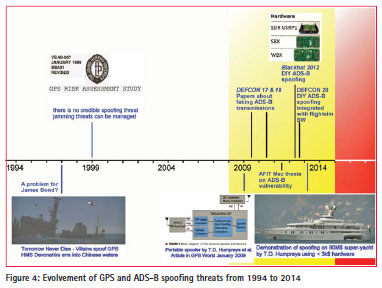
Interestingly enough, two years before experts concluded that there is no credible spoofing threat, in the 1997 James Bond Movie ‘Tomorrow Never Dies’ spoofing of GPS served as a major element in the plan of a villain to cause significant havoc. Perhaps the movie was so unrealistic that it strengthened the opinion that in reality spoofing of GPS would be impossible. It was very fitting that in 2013, Dr Humpreys actually used an 80M$ super-yacht to demonstrate feasibility of his 3k$ software-defined spoofer.
Dealing with the threats
Safety results from risk mitigation, which can comprise both engineering responses and regulation to deal with threats. In order to make the associated trade-off in a responsible way, the first requirement is that hazards are actually recognized for what they are. This requires both recognition of the threats and their potential impact.
Step 1: Recognition
Jamming and spoofing threats may have seemed unwarranted, impossible, unlikely, too difficult to realize or technically infeasible in 1999. Given that nowadays anyone can buy a GPS jammer for about 30$ through a webstore, such optimism is neither justifiable nor affordable. Since 1999, society’s dependency on the availability of accurate position and timing information has increased significantly. As a result, the consequence of a disruption will be far more severe than 15 years ago (power grids, financial transactions, aircraft navigation, surveillance, etc).
Due to the developments in software defined radio and the increase in computing power, the barrier to be passed for both GPS and ADS-B spoofing in terms of investment, effort and experience has been lowered considerably. Nowadays, the type of GPS spoofing threat that was predicted in 2003 is possible. Fortunately, the experts that have developed the required software did not release it to the general public. However, one should consider that the MP3 compression which was internally developed at the Fraunhofer laboratory was also not intended to be released. In the end, MP3 altered the landscape of the music industry. The possibility of ADS-B spoofing has been demonstrated both in Europe and the U.S.
Step 2: Identification and Classification
Similar to the fact that in 1989 few people would have expected how today’s society has become dependent on the Internet and how vulnerabilities have been exploited by criminals, it is unlikely that the experts involved in the 1999 GPS risk assessment study could have foreseen the proliferation of GPS jammers as (be it illegal) ‘consumer electronics’ and recent developments in the area of software defined spoofers. Whereas in the 1999 GPS risk assessment study, the classification was only used to judge consequences related to the use of GPS as an aid to landing, the approach has a much broader applicability. Given today’s vastly increased dependence on satellite based position and timing information, a periodic vulnerability assessment using a classification based on probability and consequence, combined with a rationale for the unacceptable combinations, should be part of any process in which systems rely on GPS or similar data, and the consequence of failure is in the category ‘major’ or worse.
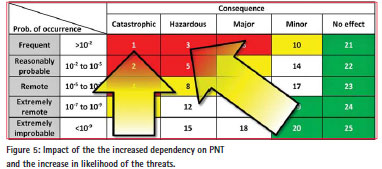
Undeniably, the likelihood of occurrence of jamming and spoofing threats has increased in the past 15 years. When looking how similar threats have increased on the Internet, there is not a single reason to assume it will not get worse. Figure 5 uses the matrix presented in Figure 3 to visualize the impact of these developments:
The vertical arrow represents the effect that due to the proliferation of jammers, the likelihood that disturbances occur has significantly increased. The slanted arrow represents the effect of society’s increased use of and dependency on accurate position and timing information, also in critical infrastructure. Due to these two developments, both the likelihood and the consequences of disturbances have become worse.
The impact of disturbances on consumer electronics will also have increased, but although consequences will be considered as a nuisance by the users, it is fair to say that in terms of safety these events belong in the category of ‘no effect’. Similarly, the impact of a local disturbance on a roadtaxing system may have (minor) financial consequences for the agency responsible for collecting the fees, but also has no effect on safety. On the other hand, it is not unlikely that people may be tempted to use jammers in an attempt to defeat a road taxing system. Depending upon which other infrastructure relying on GPS is also affected; the consequences may increase in severity. Sufficient examples exist that this is already happening today.
Step 3: Mitigation
Jamming and spoofing are illegal. As indicated in the introduction, engineering and regulation are two of the most common options for risk mitigation. Regarding the latter option, an important question concerns which part of the threat can be ‘legislated’ away.
In his keynote address at the ENC 2014, Dr Parkinson addressed the question what actions can/should be taken to reduce vulnerability and ensure PNT availability [20]. His main recommendation was to ‘Protect the clear and truthful signal, Toughen user’s receivers and Augment or substitute PNT sources’, in short: PTA. An example of a local, alternative system that is being considered to guarantee PNT availability in the harbor of Rotterdam is eDLoran [21], which has demonstrated accuracies in the order of 5 meters. Regarding legislation, Dr Parkinson recommended the increase of current U.S. penalties for jamming (fines in the order of 12 k$) to those enforced in Australia (up to five years imprisonment and/or fines approaching 1M$). In [22], a broader approach to the regulation is discussed and a range of required improvements to PNT governance are proposed. Whereas the proposed PTA approach focuses on PNT availability, solutions for the threat to integrity also have already been proposed over 10 years ago. In [12] a public key/ private key authentication architecture is described for the low-rate data stream that would enable receivers to detect spoofing attempts from data contents, rather than from signal properties only.
A comparable encryption/authentication approach could also solve the issues related to ADS-B spoofing. In [23], encryption schemes and challenges associated with implementing confidentiality security protections for the ADS-B environment are discussed. In [17], the continued development of socalled mode 5 level 2 ADS-B broadcasts (using encrypted channels) is suggested. In [19], it is recommended that: ‘for the creation of a long-term security solution in dependent air traffic surveillance, it makes sense to consider the impact of both secure broadcast authentication approaches as well as of secure location verification’.
Conclusion
This article started by identifying similarities in threats to information confidentiality, integrity and availability on the Internet to those in the navigation domain. Once the associated technology and infrastructure reached the consumer electronics domain, the resulting economy of scale reduced cost dramatically. This enabled an unprecedented creation of services that rely on the availability of PNT information, often without the user’s awareness of the threat and potential consequences. Based on the similarities with the developments of threats to information availability and integrity on the Internet, there is no reason to hope that it will not get worse. Similar to the use of encryption and authentication techniques on the Internet, the use of such techniques holds great promise to assure integrity of PNT information. Also threats to PNT availability due to jamming have been recognized over many years, and several types of solutions have been proposed. It would be most unfortunate if those responsible for safety are unaware of the existing and emerging threats or underestimate them, and as a result do not see the need for the required coordinated engineering responses and regulation as described in [20] and [22].
References
1. ICAO (1995). Report of the Special Communications/Operations Divisional Meeting, Document 9650.
2. RTCA (1997). Minimum Aviation System Performance Standards: Required Navigation Performance for Area Navigation.
3. Davis, J.M. and R.J. Kelley (1993). RNP Tunnel Concept for Precision Approach with GNSS Application. Proceedings of the ION 49th Annual Meeting, June 21-23, Cambridge, MA.
4. SESAR Consortium (2009). European Air Traffic Management Master Plan – Edition 1. 5. JPDO (2010). “Concept of Operations for the Next Generation Air Transportation System”, Version 3.1.
6. Bellovin, S.M. (1989). Security Problems in the TCP/IP Protocol Suit. Computer Communications Review, Vol. 19, No. 2, pp. 32-48.
7. Shimomura, T. and J. Markoff (1996). Takedown: The pursuit and Capture of Kevin Mitnick, America’s Most Wanted Computer Outlaw. Hyperion, ISBN 9780786889136.
8. GPS Risk Assessment Study Final Report, January 1999 M8A01 Revised. The John Hopkins University – Applied Physics Laboratory, Laurel, MD.
9. 14 CFR 25.1309 – Equipment, Systems and Installations.
10. Vulnerability Assessment of the Transportation Infrastructure Relying on the Global Positioning System – Final Report, August 29, 2001. John A. Volpe National Transportation Systems Center.
11. Tippenhauer, N.O., C. Pöpper, K.B. Rasmussen and S. Capkun (2011). On the Requirements for Successful GPS Spoofing Attacks. Proceedings of the 18th ACM Conference on Computer Communications and Security, October 17-21, Chicago, Il.
12. Scott, L. (2003). Anti-Spoofing & Authenticated Signal Architectures for Civil Navigation Systems. Proceedings of the ION GPS/GNSS Conference, 9-12 September, Portland, OR.
13. Humpreys, T.E., B.A. Ledvina, M.L. Psiaki, B.W. O’Hanlon and P.M. Kitner Jr. (2009). Assessing the Spoofing Threat. GPS World, Vol. 20, No. 9, pp. 28-38.
14. Kunkel, R. (2009). Air Traffic Control: Insecurity and ADS-B. Defcon 17, July 30 – August 2, Las Vegas, NV.
15. Haines, B. (2012). Hackers + Airplanes. No good can come of this. Defcon 20, July 26-29, Las Vegas, NV.
16. Costin, A. and A. Francillon (2012). Ghost in the Air(Traffic): On insecurity of ADS-B protocol and practical attacks on ADS-B devices. Black Hat Conference, July 21-26, Las Vegas, NV.
17. McCallie, D.L. (2011). Exploring potential ADS-B vulnerabilities in the FAA’s NEXTGEN Air Transportation System. Air Force Institute of Technology, AFIT/IWC/ENG/11-09.
18. Schafer, M., V. Lenders and I. Martinovic (2013). Experimental Analysis of Attacks on Next Generation Air Traffic Communication. In: Applied Cryptography and Network Security, pp. 253-271, Springer.
19. Strohmeier, M., V. Lenders, I. Martinovic (2014). On the Security of the Automatic Dependent Surveillance-Broadcast Protocol.
20. Parkinson, B. (2014). Assured PNT – assured world economic benefits. Keynote address at the European Navigation Conference, April 15- 17, Rotterdam, The Netherlands.
21. Van Willigen, D., R. Kellenbach, C. Dekker and W. van Buuren (2014). eDLoran – next generation of differential Loran. Proceedings of the European Navigation Conference, April 15-17, Rotterdam, The Netherlands.
22. Goward, D.A. (2014). Position, Navigation, and Timing (PNT) Governance – Required Improvements. Proceedings of the European Navigation Conference, April 15- 17, Rotterdam, The Netherlands.
23. Finke, C., J. Butts and R. Mills (2013). ADS-B encryption. Confidentiality in friendly skies. Proceedings of the Eight Annual Cyber Security and Information Intelligence Research Workshop (CSIIRW).













 (4 votes, average: 2.00 out of 5)
(4 votes, average: 2.00 out of 5)





Leave your response!