| GNSS | |
GNSS vulnerabilities: Testing the Truth
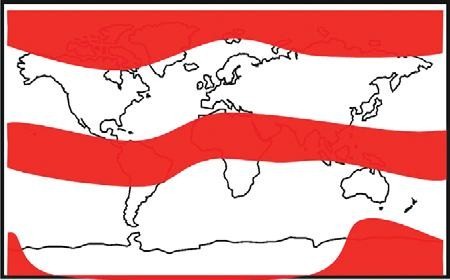
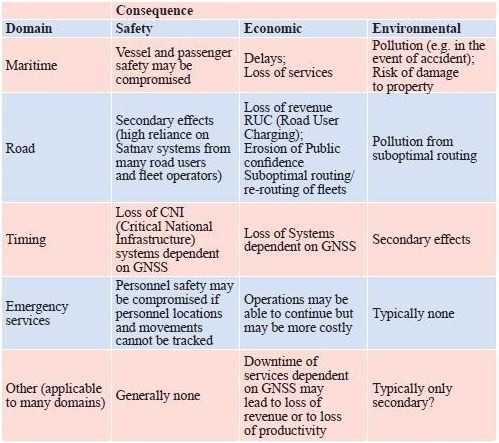
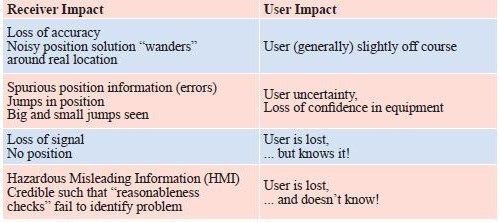
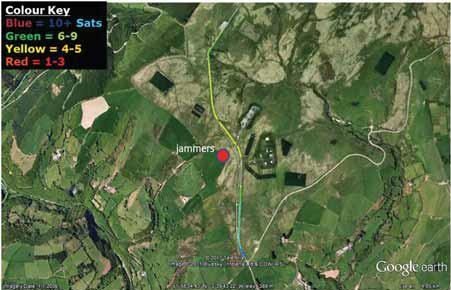
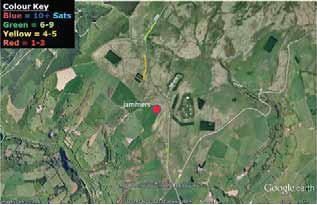
Alot has been written in the open civil domain about the vulnerabilities of GPS. The GPS system, whilst proven as extremely accurate and reliable, is vulnerable to a range of threats. Headline warnings have included the US DoT Volpe report [2] from 2001, the Royal Academy of Engineering Report [3] of 2011, interruptions to GPS-based services in some regions at the last Solar maximum, and jamming analyses conducted by the General Lighthouse Authorities [4] and many others. Prof. Last and Dr. Basker [5] even warned us at the recent ENC GNSS Conference that the vulnerabilities of GPS could lead to an increase in the price of our daily bread! Despite the warning messages, GPS has generally continued to work wonderfully well. Bread prices have been as stable as supermarket profit margins and consumer budgets dictate they should be. GPS (or to use the generic term that encompasses GLONASS, Galileo, and Beidou as well, GNSS) is global. The systems provide hundreds of millions of users around the World with a very cheap mechanism to do nearly anything that involves positioning and timing. The enormous benefits of Global Navigation Satellite System (GNSS) are compounded by the tiny price tags associated with buying and running user equipment, and there have been no catastrophes to date! Inexorably, GNSS has become embedded in transport systems (land, air, and sea), timing systems, communications systems, banking, emergency services, route finders, tolling systems, and many, many more. As a society we are already arguably critically dependent on GPS (and to a lesser, but growing, extent on the other GNSSs). The question is, do we need to wait for a catastrophe before we take action to protect ourselves against known vulnerabilities of systems based on GNSS? The threats are not theoretical ones, but have been witnessed “in the wild”. They have been recorded, quantified, written about, recreated in the laboratory and examined quite extensively in some cases. So can we afford to continue ignoring their impact on an increasing range of applications and services that are fundamental to modern life? This paper is based on a presentation [1] given to the European Navigation Conference ENC GNSS 2011, held in London in November 2011. We present an overview of threats and vulnerabilities of GNSS systems in general and with a focus at application level across a spectrum of domains. We highlight some of the important countermeasures that are already available on the market, but which are not ubiquitously used. We argue that those responsible for the procurement of equipment and services (including state and private organisations) need to devote effort to quantifying the real threats that their systems will face operationally in order to ensure that procured equipment will be effective in operation. Vulnerabilities are illuminated by results from our experiments during the Defence Science & Technology Laboratory (DSTL) live jamming trials conducted in summer 2011 as part of project VULCANO. We argue that testing of equipment, applications, and services must be conducted against test specifications aligned with the equipment’s performance specifications, and should include robustness to operational threats and vulnerabilities. Vulnerabilities and threatsDespite the good performance of GPS, there are more than a few GNSS vulnerabilities and threats. Categorisation into unintentional and intentional is sometimes done to aid understanding. Unintentional disruptions include natural phenomena such as high levels of ionospheric disturbance and solar flares, as well as man-made phenomena including system errors (satellite or signal), and unwanted radio frequency transmissions (TV, microwave communications, radar, …). Intentional disruptions are where a user is deprived of GNSS services deliberately. These include jamming / interference, and spoofing. The unintentional threats are an ongoing concern. They should not, however, be considered to be stable threats simply because they’re unintentional. The imminent “Solar Maximum” makes the situation worse, since increased levels of solar radiation will lead to increased disturbance of Earth’s ionosphere, to increased electron count and variability, and to scintillations that degrade and disrupt GNSS signals. As we write this article, NASA have reported (19th January 2012) that a potent solar flare has unleashed the biggest radiation storm since 2005 that could disrupt some satellite communications and no doubt GPS too in the polar regions. Judging from the impact seen at the last Solar Maximum around 2000, GNSS services will certainly be disrupted again by the imminent maximum. GNSS receivers will lose lock on the signals they’re tracking, resulting in outages of tens of minutes or a few hours. Oil and gas exploration services suffered the main impact in 2000. They were the only “sophisticated” users in the worst affected areas around the equator and tropics. There will be many more users in a great array of application fields this time. The other major change in unintentional threats to GNSS is the pressure on shared use of a finite radio spectrum. Communications and broadcast services march ever onwards supporting our societal growth, and with the growth in modern multi-media communications there is an ever-increasing demand for bandwidth / spectrum. “Light- Squared” is the latest, but by no means the only communications service to cause a problem to GNSS receivers. And of course, GNSS Systems, when operating on the same frequencies as each other, interfere to some extent with one another’s signals. As more systems and satellites enter the fray, the background interference worsens. Illustration of Regions most susceptible to Ionospheric Disturbance and Scintillation GPS Jammer – one of many available on the internet The threat of intentional disruptions to GNSS services is also growing. GPS is used to track both valuable cargoes and tagged offenders. It’s used in tracking devices that thwart car thieves. It’s used in some countries to measure the journeys of road vehicles in order that drivers can be billed for their motoring miles. These innovations unfortunately give criminals an incentive to interfere with GPS services: a professional car thief can continue about his business of stealing Ferraris by using a combined GPS / GSM jammer to block the car’s anti-theft system from knowing and reporting where the vehicle is. This criminal incentive, combined with the inherent innovation of humanity, has led to a substantial business for making and distributing GPS jammers. They can be bought online, or one can build one’s own from plans published on the internet! CountermeasuresThere is a vast array of countermeasures available. Here we say a few words about some of them: System-Level Countermeasures (generally these countermeasures are “out of scope” for users of GNSS Systems and applicable only to the Systems’ designers. There is however a notable exception: Systems bought with taxpayers money should deliver services that meet the needs of those taxpayers – if you perceive that System providers are not doing all they could to make your GNSS robust, then lobby them and the organisations that fund them to do better! RIN is one good rallying point for such activity.) • Multiple signals mean that if one signal is degraded then appropriately equipped users can use another instead. • Signals themselves can be transmitted at a higher power; spot beams can be used to increase incident power over a limited region. This will of course increase the impact of mutual interference to other systems. • Signal encryption / decryption and authentication of signals and data all make spoofing more difficult. Countermeasures based on Receiver Antennas • Choke ring antennas block (or at least decrease) incident power at low elevations. This reduces or eliminates the impact of any interference from low elevations as • Gain optimised antennas can do the same as can CRPA (Controlled Reception Pattern Antenna (often colloquially referred to as an antijamming antenna)) (null-steering, etc.) antennas although this technology is only widely available to the military. Receiver-based Countermeasures • Multi-system and particularly also multiple-frequency use grants a level of robustness, unless interferers also cover multiple frequencies. • Radio-Frequency Front-End (RFFE) checks can identify interference. This can be used to alert users to a problem in order that its impact can be mitigated at application level or user level. • Monitoring and filtering of interference can eliminate or mitigate its effect, and / or detect its presence at receiver level. Terminal / Application-Level Countermeasures • Hybridisation & Redundancy in simple terms means combining the GNSS navigation part with other sensors such as an Inertial Measurement Unit (IMU), compass or odometer. In the event of GNSS problems, the second (dissimilar) system takes over as the primary navigation means. • Secure interfaces and tamperproof hardware reduce the risk of physical tampering, which may be the major threat for some applications (automotive anti-theft units, fishery units that track vessels to ensure no-fishing zones are respected). Back-office Countermeasures • Prediction – direct comparison of predicted measurements (and predicted course) with reported measurements / course can be carried out in a back-office to indicate GNSS or other problems that may warrant action or investigation. • Integration of GNSS data with other data sets can again be used either in back-office or a mobile application to identify problems. Contingency Plans can also be excellent counters to GNSS threats. They are often economic and simple to implement, albeit with a degraded service level compared with that when GNSS is fully operational. The key point is to plan ahead so that they can be implemented when needed! • Wait until service resumes. In the event of a GNSS problem, do you really need to do that operation right now, or could you wait for a few minutes or hours, or go to another location? • Abandon mission. Potentially a serious decision to make, but this may be the only safe option in some cases. • Proceed using what we used before we had GPS (e.g. using visual navigation cues / using voice reporting of police officer locations / voice reporting of truck fleet location, etc.) • Use alternative techniques or routes. Application vulnerabilitiesIt can be very constructive to consider the consequence of GNSS system or application vulnerabilities in terms that are meaningful to particular users. The table below gives a simple summary for several domains of operation that were considered during the VULCANO study. It lists the consequence of vulnerabilities against three major categories – safety, economic impact, and environmental impact. Enormous complexity and depth of analysis can of course be pursued in this type of analysis, but our simple summary gives at least a feel for some of the major factors. Failures – Results from fi eld trialsDuring Summer 2011, NSL and The University of Nottingham seized the opportunities offered by the Technology Strategy Board-supported VULCANO project and by DSTL’s GPS jamming trials at Sennybridge, to examine what actually happens to real navigation equipment in real operational situations of interference. A wide selection of equipment was tested including: • Consumer grade • Commercial grade • Professional grade • Augmented (inertial, Micro Electro Mechanical Systems (MEMS),…) • GLONASS receivers • And eLORAN We had some interesting findings, some of which were presented at the ENC GNSS conference in Autumn 2011. After the presentation, one questioner asked me “what did you see that was unexpected?” Unfortunately, my questioner had missed the point. What I might expect as a navigation expert of a quarter century standing when I go to GNSS jamming trials is one thing. Surprisingly enough that will not be the same thing as the expectations of the poor fellow going about his daily business, relying (perhaps even unknowingly) on GPS, and not thinking nor indeed even knowing about jamming at all. Most of the population are not navigation experts. Most believe that jamming is something that Auntie Katie does when she isn’t marmalading! One of the Jammers Nottingham Geospatial Institute’s Trials vehicle In the relatively controlled environment of the wet and windy Welsh hills, with the relatively friendly DSTL jamming set-up, what we saw is what you, dear reader, could experience with your GPS equipment out in the real world when you’re using GPS to (a) guide your private plane or (b) wondering what’s happened to the high-value cargo you thought you were tracking in your armoured car, or (c) whatever real- World application you have. Suddenly interference or jamming or high levels of ionospheric disturbance will cause the same effects we saw, but in a situation where you’re not expecting it. If you have no countermeasures and no fall-back, you might suffer extreme consequences resulting from your loss! Indeed, you might not even notice there’s a problem because there’s a very high probability that your current-generation GNSS equipment will not report it to you! At the very least, you might notice when you’ve lost your way, run aground or can’t find your armoured car on the map. Amongst other things our equipment suffered the problems shown in the table below. The impact at receiver level is listed, along with likely impact at user level. The user level impact is often the more meaningful one for anyone who isn’t a GNSS equipment designer, but is of course dependent on what impact is suffered at receiver level. User Impact is also highly application specific. Position jumps may be annoying to surveyors and have to be post-processed out as outliers. The same position jumps could also lead autopilot equipment to alter course, which could be rather more serious. Jamming test (lower power) – Vehicle drove along the road, suffering a loss of satellites (and position) close to the jammer. The coloured line shows the recorded track with colour indicating the number of satellites tracked. As we continued away from the jammer satellites were recovered and navigation regained. Testing robustnessIf we need systems based on GNSS that are robust against threats & vulnerabilities, then we need to specify what they must be robust against – i.e. a threat specification and recording of vulnerability testing. It included: • Test regime • Equipment under test • Mode (acquisition, re-acquisition, and tracking behaviour may be very different) • Conditions to test (specification) • Test Equipment • Jammer types, powers, characteristics, other threats, … • Monitor equipment • Test Process (Specific steps) • Outcome • Expected • Observed • Findings, Conclusions, Recommendations The Test equipment is obviously rather specialised. Simulators and live jammers along with anechoic test environments are all part of the paraphernalia. Much of this equipment already exists in military circles; less exists outside those circles. GRACE, with its mandate to support GNSS testing in the UK is developing test types, procedures, resources and success criteria as well as tools required to assess GNSS vulnerabilities, and highlighting the need for test specifications for operationally realistic threat scenarios. This is the latest part of the story of industrial and institutional efforts to define UK needs for GNSS Testing (acknowledging efforts from organisations and individual participants in UKSpace, Intellect, and the Digital Systems KTN, as well as the 2011 Royal Academy of Engineering Report on GNSS Reliance & Vulnerabilities). Jamming test (higher power) – vehicle drove along the road and almost immediately suffered impacts from the jamming. Position was reported off-road by 10’s of metres (the vehicle never left the road); at other times no position was available. ConclusionsGNSS vulnerabilities are many and varied and include natural and man-made threats. Some are getting worse (imminent solar maximum, spectrum demand, low-price jammers coupled with incentives to use them). The impacts can be serious on a huge array of user applications. Do we really need to wait for a catastrophe before taking action against GNSS vulnerabilities? Many countermeasures already exist. Their effectiveness against threats is variable – some are effective against one threat but not another. Some countermeasures are more applicable to certain applications than to others due to factors such as cost, size, weight, and form factor. Countermeasures will of course be more effective where users mandate their inclusion in GNSS products; if users are complacent then we can only assume that suppliers will be too, since they have little incentive for action. In our opinion users need to assess the vulnerabilities of their applications, and need to create procurement specifications that specify actual operational needs, including robustness. End Users may need to engage specialist support to ensure that new equipment is not only cost-effective but operationally effective too! To support this, threat analyses, including characterisation of both unintentional and intentional threats needs to be published in order that they can be protected against. References1. Dixon, C.S., C.J Hill, M. Dumville, Dr. D. Lowe; The Testing Truth of GNSS Vulnerabilities. ENC GNSS 2011 Conference, London, Nov.29 – Dec.1, 2011. AcknowledgementsThis paper is based on a presentation given at the European Navigation Conference ENC GNSS 2011, held in London in November and December 2011. The experimental work reported here was carried out by staff from two partner organisations working together in the VULCANO Project. The industrial leaders were Nottingham Scientific Limited and the academic partners were from the University of Nottingham, and specifically from the GNSS Research and Applications Centre of Excellence (GRACE) and the Nottingham Geospatial Institute (NGI). Project VULCANO was supported by the Technology Strategy Board as part of their competition “Feasibility Studies for Innovation in Space”. The field tests of GNSS equipment were conducted as part of the Jamming Exercises run by DSTL at Sennybridge during summer 2011.
|

















 (9 votes, average: 2.89 out of 5)
(9 votes, average: 2.89 out of 5)




Leave your response!