| Policy | |
Location and privacy issues
 |
|
|||||
The very capabilities of geospatial tools in information analysis have raised a multitude of novel and interesting personal privacy issues |
|
The tools of GI Science deal with geospatial information in which spatial relationships are the fundamental data. Fundamental data is that which relates to geolocation or spatial data that will permit the mapping of any object in terrestrial space. But, GI Science may also handle a diverse range of personal information from the truly ‘personal’ ones through to those of a more general nature – age, gender, height, home address, social security number, marital status, religion and so on. By its very nature, the tools of GI Science allow these kinds of information to be collected, manipulated, displayed, and transmitted cheaply, easily and speedily. But the very capabilities of geospatial tools in information analysis have raised a multitude of novel and interesting personal privacy issues.
The challenge
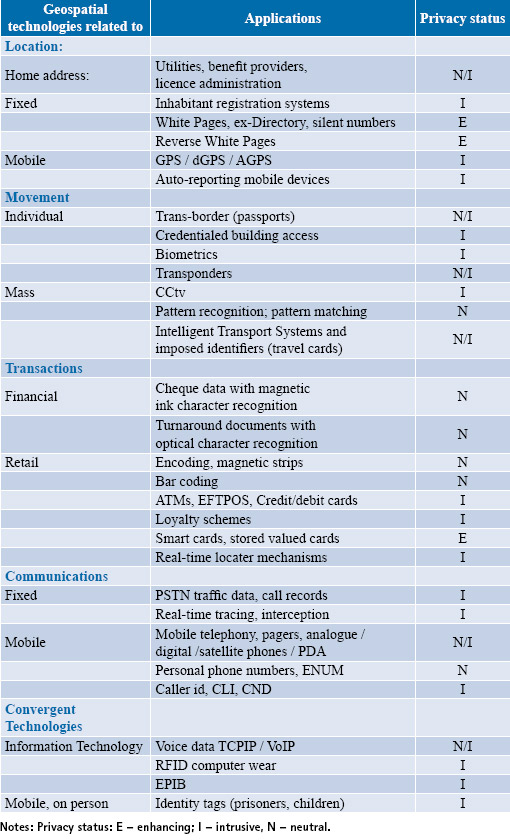
The challenge for geographers and geospatial scientists is to accommodate the privacy-invasive with the privacyenhancing attributes of geospatial science as summarised in Table 1 below. If these are attempted in an ethical manner then it augurs well for geospatial information systems and the professionals who work in the industry. Dobson (1998) promotes the view that geo-information in combination with personal information clearly poses a privacy threat. However, the counter argument is that there is a tension between the two fundamental values of privacy on the one hand and the public’s right to know on the other. For example, the differences between satellites monitoring a farmer’s use of water and the public’s acceptance of CCtv and video cameras in shopping malls, buses and taxis, city streets and in dorms and apartments.
Geospatial technologies and ethical use
Geospatial technologies include GIS as a mapping tool for decision-making through to those technologies that amass data by spatial attributes including global positioning systems (GPS), and transponders and other intelligent computer chips embedded in some devices that can report location as well as an identity. The latter are in a class of intelligent spatial technologies that can declare both personal information as well as locational and devicespecific information in response to a poll by another device either in a preestablished relationship or to a new, soon to be established, relationship.
Geospatial technologies are in daily use and have heightened personal privacy concerns related to locational information. For instance, in using geospatial technologies, an apparent legal fallacy may have arisen, if only by accident. The idea is that if there is a legal right to do something then it follows that it must be the right thing to do. So, if it is legal to install CCtv anywhere, it is permissible to do so despite the fact that constructing too many of these devices might become too intrusive.
Also, if it is permissible to undertake data aggregation activities using a number of databases, then it is lawful to do so. But really, the issue is that the legal right must only be the starting point rather than the end point for justifying one’s actions. The fact that something is legal does not mean it is either right or a wise thing to do. Thus, data taken out of context – acontextual data – and used in that sense may produce results that may be highly unjust and totally incorrect in particular cases.
This is where ethical questions are raised and which should be foremost in the thinking and practice of GI scientists. Some would like to consider ethics as a continuum in which there is both a duality of a right and a wrong way of undertaking activities as well as ethics as a way of dealing with a right way and a better way of doing things. In equitable jurisdictions and civil cases there may be a claim to a right but it is the one who has the better claim that often wins out. Today the right to be left alone is being vigorously defended and there is resistance to increased surveillance in parts of our private lives. But it seems that the real threat is the creeping acquiescence to all sorts of intrusions without the accompanying public debate, information and education. It used to be that when a video camera was installed, say in the computer lab, the spectre of George Orwell’s 1984 and “Big Brother is watching you” was raised (Orwell 1990).
GIS is not personal data intensive
Flaherty (1994) in relating his experiences with privacy protection and GIS in a national and provincial context has said that GIS technology is “not personal data intensive” and that information privacy issues are always solvable by applying fair information practices.
GIS has the power to integrate diverse information from multiple sources. Some of the data are of a personal nature where individuals may be identified or identifiable while others are of a spatial nature that may be used to locate individuals through geocoded data such as a home address. The privacy threat is from the new inferences that may be made by correlating geographic information with personal information.
Privacy
But what is privacy? Professor Arthur Miller of the Beckman Center for Internet and Society, Harvard Law School has described privacy as an intensely, perhaps uniquely, personal value. The word stems from a Latin root privare which means “to separate”. To want privacy is to want to be separate, to be individual. Another meaning of the Latin is “to deprive”, and privacy also means leaving something behind (See Beckman Center for Internet and Society and in particular the course syllabus for ‘Privacy in Cyberspace’ at http://eon.law. harvard.edu/privacy99/ syllabus.html).
Indeed Roger Clarke (1999) has identified four privacy interests – information, territorial, bodily and communications privacy. Information privacy relates to the interests of the individual in controlling the information held by others about that person while territorial privacy is the interest in controlling intrusion into aspects of behaviour especially in regards to sensitive issues. Bodily privacy is the freedom from interference with one’s person while communications privacy is the freedom from surveillance and privacy of communications.
Location-based services
Location-based services (LBS) rely on the key ingredients of time and space. LBS may be considered to be no different from geodemographics, an information technology that enables marketers to predict behavioural responses of consumers based on statistical models of identity and residential location (Goss 1994, 1995).
LBS have become commonplace because of the use of geocodes and GPS and other mobile communication and tracking technologies. LBS inferentially involves the tracking of people through the use of credit card data that may result in profiling exercises, statistical modelling, and pattern analysis. More generally, GI Science using such technologies may give the game away as to who we are, where we are, and what we have been doing either by way of speech, purchases or simply being at a location. There is one view that without legislation to curb the (mis)use of such data there would be chaos. However, an equally compelling but opposing view is that there should be no legislation but rather just self-regulation by industry itself (Westin 1967, 1971).
Data aggregation and databases
Private sector commercial applications of both GIS and LBS are perhaps the fastest growing areas of business and this has fed the need for more data. For example, in order to maintain a competitive edge, marketers need good databases to make their decisions while simultaneously handling geographical data efficiently. Patterns, relationships, and trends become clearer when depicted visually in graphs, charts, and maps rather than just columns of numbers or text.
A database called EQUIS, developed by the US National Decision Systems, “maintains a database of financial information for over 100 million Americans on more than 340 characteristics including age, marital status, residential relocation history, credit card activity, buying activity, credit relationships (by number and type), bankruptcies, and liens. This information is updated continuously at a rate of over 15 million changes per day,” (Curry 1992, p. 264).
In 1993, Equifax and National Decision Systems announced Infomark-GIS – a fully integrated GIS specifically designed for marketing applications and decisionmaking (Equifax National Decision Systems 1993). There are also other U.S. companies are also engaged in the collection, processing and storage of data pertaining to individuals (A search of those firms classified under the Standard Industrial Classification (SIC) code 7374 for companies engaged in marketing and business research services yielded approximately 50 companies). These firms obtain consumer information from credit bureaus, public records, telephone records, professional directories, surveys, customer lists and other data aggregators.
In view of the commercial market for data, databases and data aggregation services, Curry (1994) has suggested that the use of geospatial technologies will produce multifaceted problems that would similarly require multi-dimensional solutions. The concerns raised include the fact that the technologies consist of and promote the widespread availability of unregulated data. This leads to the difficulty of regulating data matching that must take place if the geospatial tools are to produce meaningful results. Further, geospatial technology is inherently visual but this strength also exposes a major weakness in that it may produce map inferences that may be both statistically and ecologically fallacious. Finally, there is the altered expectation of privacy rights because the case law may promote an erosion of those aspects of life where a person can feel safe, secure from search and surveillance, and most importantly information kept private.
Geospatial technologies are said to do best at the intersection of location, time, and content. But each of these elements of location, time, and content tends to produce tensions of their own. For example, in regard to letting people know where they may be and to keep this fact hidden because they may not wish to be found. Here we have a technology that is employing the power of the ‘place’. GISbased geostatistical models using locations and space have been used to study the home range of animals, for instance. In an analogous way, geographical profiling may be applied to the “home range” of predatory humans who may have inadvertently patterned habitual routes when stalking potential victims.
Leipnik et al. (2001) reported on the important role of geospatial technologies in investigating and gathering evidence of a locational nature in order to convict a serial killer. When the serial killer Robert Lee Yates was arrested in April 2000 in Spokane County, Washington State, he is reported to have told his wife to “destroy the GPS receiver.” This was because there were incriminating data on it showing the 72 waypoints associated with several journeys that had been used in disposing the bodies of the victims. Indeed, this example demonstrates the extent to which GIS and GPS technologies are permeating society and their use – both by law enforcement agencies as well as criminals. However, a court appeal could challenge the validity and use of the GPS data. The argument could be that using the GPS to track suspects without their knowledge might involve an invasion of privacy rights as well as not meet the legal test of finding the “least obtrusive means” for police to gather information about a suspect. But, in counter argument, it may be submitted that sometimes consent needs to be conspicuously absent in cases where suspicions of the ‘quarry’ are not to be aroused prematurely.
The question may be asked: Is there any special data protection or privacy issue associated with locational data? The answer is YES but its explanation must be given indirectly. “Sensitive personal data” is regarded as data that identifies, among others, a person’s ethnic background, religion, political affiliations or sexual habits. However, the location of a person is not considered sensitive personal data. Yet, when processing data on persons, especially when locations are involved, say in terms of visiting synagogues on a regular basis or particular areas of ethnic concentrations, it is arguable that sensitive data are being processed and unintended inferences are being made about a person’s religion or ethnicity (Rowe and McGilligan 2001).
Location, tracking and dataveillance
Most geographers will understand location to mean the relative positions of entities in space and time and of events taking place. Locational information describes a person’s or entity’s whereabouts in relation to other known objects or reference points. In this context, tracking is meant the plotting of the trail or sequence of locations within a space that is taken by an entity over a period of time. The “space” within which the entity’s location is tracked can be a physical or a geographical space. However, such a space can also be ‘virtual’ where that person may have had successive interactions in time with different people either simultaneously or at different times.
Data surveillance, abbreviated to dataveillance, is the systematic use of personal data in the investigation or monitoring of actions or communications of one or more persons. Conceptually there may be two separate classes. Personal surveillance is the surveillance of identified persons for various purposes. This may include investigation, monitoring or gathering information to deter particular actions by that person or particular behaviours of that person. Mass surveillance, on the other hand, is the surveillance of large groups of people, again for the purpose of investigation or monitoring and which may aid in the identification of persons of interest that a surveillance organisation has cause for concern (Clarke 1999a).
Geospatial technology applications: Home location
While geospatial applications based on remote sensing of the earth on regional scales, and the use of GIS in very small scale city planning are relatively well-known, the application of such technologies to home location are less prominent. In general, utility companies may use home location data to track usage of power, gas and water, whereas social security benefit providers and licence administrators may make use of street addresses to tag locations for administrative purposes.
Telecommunication services to the home via the double-twisted copper wire provide home location information to the Public Switched Telephone Network (PSTN) of a phone utility. All phone communications to and from the home address can be recorded, stored, analysed and made available to others. Telephone traffic data may be analysed as call records and have been used for billing and invoicing purposes. The data also give paired locational information of the origin and destination of calls (dyads) that may be analysed for particular information.
More recently home telephone services have facilities such as caller ID, calling line ID (CLI), and calling number display (CND) that give information of a caller, the caller’s phone number, and the time of the call. Caller, line, and number identifications are now generally available and have been used by telecommunication companies, law enforcement agencies and consumers as a means of screening calls.
Australia on Disk (AOD) is a directory of every residential and business phone number in the country. This comprises all 55 national phone directories giving a total of 1.3 million business listings and 6.9 million residential phone numbers in 2005. While there are obvious environmental benefits in not having to produce paper copies of telephone directories, there are equally potent privacy implications not to do so given that a disk containing residential information may be put to other than legitimate uses (Each year in Australia Sensis/Telstra produces about 55,000 tonnes of directories or 18 million sets of Yellow Pages and White Pages of which 80 per cent is recycled. But that still means about 11,000 tonnes go into landfills each year. See Lowe S 1994 ‘Indecent disclosures’, The Sydney Morning Herald, 21 March, p. 47). The information obtained can then be used to individually address letters to be sent out or used in a phone marketing campaign. An additional product, the AOD Mapper presents data and maps with areas of interest colourcoded to show their relative importance. The maps could identify hotspots where the residents are most likely to match particular profiles, for example, the suitbuying yuppie, the private school targeting high-income earners with young families or health insurance companies looking for low risk, single, professionals.31 Tracking movements of individuals over space The tracking of individuals over borders has normally been controlled and monitored at immigration counters by checking and stamping national passports and the use of identity cards. More recently such travel documents have electronic chips embedded in them that permit electronic scanning and automatically provide entry and egress at checkpoints. The data captured may yield patterns of entry and departure of citizens and visitors alike. At a microscale, movements within buildings may be monitored using video surveillance equipment. In combination with video evidence, movement over time and space within buildings, analyses using pattern recognition and/or matching algorithms may yield greater insights to movement patterns of individuals or groups of people and the most trafficked areas. However, while the system may provide greater effectiveness to the security of a particular building, the technology is highly intrusive of the privacy of its users.
In Malaysia, for example, the introduction of the Government Multipurpose Card (GMPC) or MyKad is a standard credit-card-sized plastic token with an embedded microchip. MyKad has been issued progressively since 2001 with the mandatory obligation that everyone in the population 18 years and over should have one. To date, it seems that this is the world’s first national smart card scheme that stores biometric data on an in-built computer chip. The encoding is a copy of the owner’s fingerprints. But there have been niggling misgivings, for example the practice of surrendering identity cards to security guards before entering certain premises or ‘gated’ communities would require close monitoring because of privacy concerns (Idrus 2003).
A layer of privacy protection has been installed with the passing of the Personal Data Protection Act (2002) with safeguards including the appointment of a Data Protection Commissioner. However, the Act has yet to come into full effect on the grounds that it will be a burden to businesses. There are no other safeguards against the abuse and privacy of data for MyKad. In general the Malaysian Constitution does not provide for the protection of privacy (The National Registration Act (1959) provides for the establishment and maintenance of a registry of all persons in Malaysia (s 4) and that every person in Malaysia be registered under the Act (s 5). The Register extends to all residents of Malaysia, including non-citizens who work and reside there). Article 5(1) of the Malaysian Constitution provides the fundamental guarantee that “no person shall be deprived of his life or personal liberty, save in accordance with law”.
In Australia the Hawke government attempted to introduce the Australia Card in the late 1980s but there has been general resistance and outright opposition (see Davies 1996). A health card of sorts was also proposed in Australia which met with strong opposition by the population (see HIC 1985).
Elsewhere in Hong Kong, concerns about information privacy have been raised in terms of the HK Smart Id Card. This was because of the possibility that one card could bring together a comprehensive personal dossier from different sources relating to an individual. (See HK Privacy Commissioner 2000).
Tracking transactions
There have been a variety of methods used to capture transaction data. These include cheques that carry data in MICR – magnetic ink character recognition and turnaround documents with OCR – optical character recognition where the form has already been filled-in automatically for the client to authenticate and return. Other means of data capture are magnetic strips, embossed data codes, bar coding or a device with a location identity such as a phone socket in the home environment. The main applications are in financial transactions from deposits, to loan repayments, salaries, cash withdrawals at automatic teller machines (ATMs), use of credit/debit cards and electronic funds transfer-point of sale (EFTPOS) and others. These seemingly helpful and efficacious systems, however, turn previously unrecorded and/or anonymous activities into recorded-identified transactions. Even more important, the data are being aggregated in a far more intense manner than before and these data have a location tag associated with it in the data trail. There are also real-time location mechanisms built into some of these electronic transaction tools so that passive monitoring and surveillance can now be re-purposed for law enforcement activities.
Tracing communications
While locational information and address tags may be readily available when using the PSTN, mobile telephony services including the use of pagers, personal digital assistants (PDAs), analogue/digital and satellite phones make the tracing of persons and locations difficult. With mobile telephony, the tracing of a device and its usage either in real-time or loggedin message banks is more difficult because its location is constantly changing.
Convergence of locational and tracking technologies
By far, the technology of most relevance for present discussion is GPS. This technology depends on a constellation of satellites to give positional information in four dimensions – latitude, longitude, altitude and time. With the Presidential edict of turning off selective availability (SA) – the purposeful degrading of positional information – users of GPS are now able to poll satellites for positional information and be given references to within a meter of their location (The White House, Office of the Press Secretary 2000 ‘Statement by the President regarding the United States’ decision to stop degrading global positioning system accuracy’, 1 May at http://www.ostp.gov/html/0053_2. html). Differential GPS (dGPS) uses the same technology except that locations are determined as a differential to the data received in addition to and relative to a surveyed point on the ground. Hence, the accuracy obtained by dGPS methods can be quite precise. Assisted GPS (AGPS) technology, on the other hand, has been developed in conjunction with information communication technology (ICT) which uses a server at a known geographical location in the network. This information reduces the time, complexity and power required in determining location.
RFID is an abbreviation for radio frequency identification, a technology similar to bar code identification. With RFID, the electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum is used to transmit signals. RFID systems can be used just about anywhere, from clothing tags to missiles to pet tags to food – anywhere a unique identification system is needed (See Webopedia definition of RFID at http://www.webopedia.com).
Conclusions
Analyses of geospatial applications with regard to home location, the tracking of individuals over space, tracing financial transactions and communications has identified privacy risks inherent in the use of such technologies. The identified privacy risks may be categorised as invasive, enhancing, or sympathetic as demonstrated in Table 1. The implications for user organisations is that geospatial technology applications is but one of the array of different kinds of surveillance and in particular that of dataveillance. Equally, technology providers should be reminded of these sorts of privacy issues and to genuinely strive for anonymity in the use of personal information when marketing their products.
The implications for policy makers including privacy and data protection commissioners is one where the tensions between economic rationalism and the social good is stretched and seemingly irreconcilable. But this need not be the case if governments are focused on both law and order, as well as striving for stability, consistency, and sensitivity that are supportive of privacy protection.
Geospatial technologies such as LBS may ‘push’ content but at the same time ‘pull’ in locational information. Use of these should not have a chilling effect on personal behaviours or actions. That effect may only be apparent where there is the danger of the acontextual use of personal information and data. Hence, it is imperative that the idea of a ‘zone of privacy’ around one’s personal and private affairs should be fostered and encouraged so that the onus is on those who intrude into the zone to justify their conduct. This zone will then demarcate a boundary to a private and a ‘public’ area with a nebula in between where everyone can interact and relate with each other and for technology to be freely used. Privacy need no longer be “too indefinite a concept to sire a justifiable issue” (Tapper 1989, p. 325).
While technology will continue to be both a problem and a solution, technological advances such as LBS, geoinformatics and GI Science will continue to push the privacy envelope. But technological means alone cannot help manage and enhance privacy protection. Legislation, corporate policy, and social norms may, in the final analysis, eventually dictate the use of location information generated from tracking devices and geospatial technologies.
Fair information practices are the cornerstone of many privacy laws today. However, these practices may be found wanting especially when they have to deal with data manipulation using disparate databases joined together in geospatial technologies such as a GIS. The solutions may lie in a mix of international standards, self-regulation, legislation, and government policy. While the harmonisation of laws and regulations and getting consistency of privacy protection especially across all jurisdictions is very difficult to achieve, yet, international standards must, of necessity, emerge. One way forward would be to keep canvassing for a global convergence of privacy regulation. It is may be counter-productive for each country to impose a separate privacy regime. We are all responsible for keeping an eye on the world in order to prevent abuse of surveillance technologies not by government regulation but by a mutual, shared responsibility for the world in which we live and disdain for those who abuse and misuse the privilege (Waters 2000).
The paper with detailed references can be seen at www.mycoordinates.org
My Coordinates |
EDITORIAL |
|
His Coordinates |
|
|
News |
INDUSTRY | GPS | GALILEO UPDATE | LBS | GIS | REMOTE SENSING |
|
Mark your calendar |
JANUARY to SEPTEMBER 2008 |












 (33 votes, average: 4.70 out of 5)
(33 votes, average: 4.70 out of 5)




Leave your response!