| GNSS | |
Evolving GNSS threats – just the tip of an iceberg?
If more people knew just how vulnerable GNSS is, and how much today’s world depends on it, they would be frightened |
 |
|
When you think about it, GNSS is miraculous. Actually, like most magic, it is best for most people not to think too much about it. They just accept that today’s cars know where they are and how to get where they want, that a cell phone knows how close they are to local restaurants, that planes can land safely in thick fog, and that ATMs and a host of other services can be trusted to deliver.
There are plenty of other miracles around, but they are somehow easier to grasp: television comes by cable or a visible aerial, cell phones rely on towers and signals break up when you get too far from a tower. Most people do have a vague idea that GNSS depends on a satellite, but have little idea of just how delicate is its operation, and that it actually depends on multiple satellites to build its accurate location data.
If more people knew just how vulnerable GNSS is, and how much today’s world depends on it, they would be frightened. And that is why we should analyse the possible threats – see Figure 1 – and suggest better strategies to protect against them.
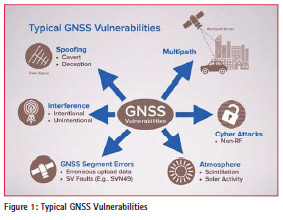
The threats can be broadly divided into natural and man-made, and the second category includes both accidental threats caused by human error, and deliberate criminal activity, terrorism or acts of war.
Natural threats in the atmosphere
GNSS signals must pass through the atmosphere and all its variations and perturbations. Weather systems can cause small variations in signal delay, while more serious changes can occur in the ionosphere, especially during increased activity from sunspots and solar flares. Over the equator and near the poles small perturbations in the ionosphere – called “scintillation” – can cause the GNSS signals to break up or the receivers see rapid variation in both signal phase and amplitude and, if not designed robustly, they can lose signal lock.
Small variations like this are not uncommon, and some GPS receivers were affected by a couple of solar events in June last year. More serious solar radio bursts during December 2006 were about 10 times larger than any previously reported event and civilian dual frequency GPS receivers were quite severely affected. Experts estimate that once in around 200 years we can experience a “Carrington event” superstorm that would cause severe and long lasting damage: the last one was recorded in 1859. A nuclear explosion in the upper atmosphere would have a similar effect, and cause propagation anomalies for weeks afterwards.
Natural threats on the ground – multipath errors
One effect from scintillation is that the receiver picks up a double signal from two different paths through the atmosphere. A similar “multipath” error can be caused by reflection: GNSS signals can reflect off relatively distant buildings, and cause gross errors if the receiver locks onto the reflected instead of the direct signal. More subtle errors arise when the reflective objects are closer and the direct and reflected signals merge.
Multipath is a well known problem and receiver manufacturers have introduced all kinds of measures including multipath rejecting antennas, receiver filtering and processing techniques. But multipath can still cause surprising errors of tens to hundreds of metres, and it is also one of the most significant challenges faced by driverless car navigation.
Accidental interference
High power transmitters, ultra wideband radar, television, VHF, mobile satellite services and personal electronic devices can all interfere with delicate GNSS signals – even causing complete loss of lock. In 2002 a poorly installed CCTV camera in Douglas, Isle of Man, caused GPS within a kilometre to be blocked.
Accidental jamming can occur when an older model GPS antenna rebroadcasts the signal on account of poor impedance matching in the amplified signal path from the low noise amplifier, and this interferes with reception in an adjacent antenna. To avoid this risk, antennas should not be mounted too close together.
In April 2005 a military GPS jamming exercise in Southern Idaho was announced in a Notice to Airmen (NOTAM) but a lot of other GPS users never heard about it until too late. Local farmers were caught out and truck and tractor drivers were forced to sit idle waiting for the GPS signals to return. A commercial crop-spraying helicopter company also lost business.
Human error
Such is the “magic” of GNSS location that people soon learn to trust it and ultimately may cease to question its data. But however good the GNSS, human error can still make nonsense of its output.
Pages of data – including the clock predictions and precise orbit predictions (ephemeris) – have to be uploaded to GPS satellites. If bad data were to be uploaded to a satellite, errors could show up as soon as the ephemeris data loads – typically every 2 hours – or they could slowly accumulate over time. It is theoretically possible that bad input could cause all the satellites to transmit bad navigation data simultaneously, causing GPS receivers to fail everywhere. Bad GPS data uploads happened in June 2002, March 2000 and March 1993, for example, but without serious consequences.
At the other end of the data stream, people can be so sure of the GNSS system that they fail to allow common sense to over-ride its data. In March 2014 the 80 metre MV Danio ran aground off the coast of Northumberland and the six crew members were stuck on board for a fortnight because bad weather postponed rescue attempts. The navigator was relying entirely on a low cost, unapproved GPS chart plotter, had not switched on the alarm system and then fell asleep.
Satellite system error
Even without human mistakes, GNSS can generate errors. The satellite’s precise atomic clocks sometimes produce errors that accumulate before being noticed. On 1st January 2004, the clock on GPS satellite SVN-23 drifted for 3 hours before the command centre marked it unhealthy, by which time the range error had grown to 300 km.
A fault in the signal modulation or generation process on a satellite, can result in bad signals that confuse receivers. The so-called ‘evil waveform’ from GPS satellite SVN 19 in 1993 caused an error of up to 8 metres, while a piggy-back L5 signal generator on GPS SVN 49 led to an on board multipath effect that caused variable, sometimes substantial errors in receivers at different elevation angles.
Deliberate signal jamming
The crudest form of jamming simply transmits a noise signal to overload the GNSS receiver and cause loss of lock. Circuits and assembly instructions for simple jammers are widely available on the Internet. Commercial jammers can be bought for less than £20 and are increasingly sophisticated: some are designed to fit into a pocket, some into car lighter sockets; most jammers are designed to block GPS, GLONASS and GALILEO (even before GALILEO is operational), others include cell phone jamming as well, while more powerful jammers, up to at least 25W, are also available.
Short of cyber war or terrorism, why would anyone want to jam a GNSS signal? As an advertisement from Jammer4U puts it: “If you are sales personnel and delivery drivers, this GPS tracking jammer is a very popular item for you to take lunch or make a personal stop outside of your territory or route off the radar We are a GPS jammer factory! We will check the quality before shipped! Best service!”
Deliberate jamming is against the law and is used by car thieves, road toll evaders, tracker evaders, lorry drivers bypassing commercial mileage limits as well as those wanting a short respite from the fleet operator’s vigilance – as suggested in the above advertisement. The jamming will typically be indiscriminate and both moving and stationary. It may be fairly low power just to defeat the localised vehicle location system but a car thief is unlikely to be concerned with managing power levels to minimise risk to other GPS users.
GNSS spoofing
Spoofing is more sophisticated than simply jamming a signal with noise, because it requires the attacker to generate realistic but false GNSS signals. Until recently it was assumed that spoofing would require specialist knowledge of GPS, whereas criminals would prefer simple, fool-proof methods. So spoofing attacks were not expected for the near future.
All that changed at last year’s DEFCON 23 hacking conference in Las Vegas, when two hackers – neither of whom were GPS specialists – demonstrated how they had created a low-cost GPS emulator using cheap off-the-shelf components and open source code from the Internet.
They made two well-known brands of smart phone show wrong location and timing information – one showed a time and date in the future. They also spoofed a car satellite navigation system into showing its position as being in the middle of Namco Lake. They also showed that they could bring down a drone by fooling its receiver into thinking it was positioned in a forbidden, geo-fenced area. Existing GPS receivers in important devices were all too willing to lock onto these fake signals without sounding any warning. The equipment needed could be bought for less than $1000, and the availability of Open Source software tools meant that the level of expertise needed was a lot lower than previously believed.
A Windward report claims a 59% increase in such GPS manipulation between mid 2013 and mid 2014, with similar motives to those described for jamming, but more typically used by ships rather than lorries. The Automatic Identification System (AIS) is used on ships for identifying and locating vessels by electronically exchanging data with other nearby ships. Vessels fitted with AIS transceivers and transponders can be tracked by AIS base stations located along coast lines or, when out of range of terrestrial networks, through a growing number of satellites that are fitted with special AIS receivers. The International Maritime Organization’s International Convention for the Safety of Life at Sea requires AIS to be fitted aboard all international voyaging ships of 300 or more gross tonnage, and all passenger ships regardless of size.
The tip of an iceberg?
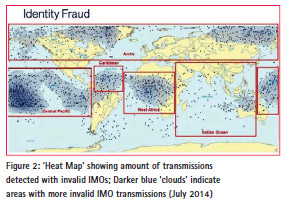
There are many reasons for a ship wanting to bypass the system. These include fishing vessels wanting to poach in forbidden territory, for smuggling and people trafficking. Other possible uses for spoofing signals could be for pirates to lure a ship into dangerous waters by issuing fake distress or man overboard signals, to make a stolen ship invisible, to create malicious weather forecasts, and impersonating a port authority. Just how widespread is this form of fraud? Figure 2 shows the distribution of false International Maritime Organisation signals detected in the year to mid 2014.
Figure 2 shows a surprising number of vessels claiming to sail across known deserts and jungles, while Britain is left relatively undisturbed. So it is interesting to note some of the GNSS interference events detected in a very quiet rural location: the Spirent facility in Paignton, Devon – surely an ideal location for GPS testing in an unpolluted radio frequency environment.
Between May and August 2015 over 100 interference events were detected. Some occurred so regularly by the clock that it is assumed that they could be caused by local machinery, some were quite mysterious, probably from a natural source and not a jammer, and then there was the off deliberate jammer signal – one lasted 3 minutes and was presumably from a van making a nearby delivery.
What should be done?
There is no shortage of incentives for GNSS fraud. Further possibilities could be to avoid GPS based road tolling systems and to outsmart location-based payment authentication services – what if one could withdraw money from an ATM while having a GPS alibi claiming that you were elsewhere when the transaction took place? A recent development has been the use of smart phone tracking as a source of forensic evidence: the police will take a suspect’s smart phone to search its movement tracking record. If that record could be falsified, then again it would provide a powerful false alibi.
So we should be mindful of the enormous potential risks and the need for better guidance to help non-specialist GNSS/ GPS users to assess the risks, known how much protection is needed, and how much would be truly cost-effective. If there were recognised global standards for robustness levels and types of risk, the buyer could make a more educated choice based on the actual need, relative risk and additional cost.
Controlled testing, under a range of realistic or extreme operating or attack conditions, helps manufacturers to develop more robust systems – standardized tests against set criteria are improving the performance and reducing vulnerability. A recognized set of standard tests will make it easier and quicker for customers to select the best equipment for their application based on performance and levels of protection
The time is ripe for sharing ideas before we hit the iceberg. There is a GNSS Vulnerabilities group on LinkedIn specifically for discussing issues around GNSS jamming and spoofing. Join it.












 (4 votes, average: 4.75 out of 5)
(4 votes, average: 4.75 out of 5)




Leave your response!